Its High Time to Focus on API Testing Proactively
27th July 2021, Kathmandu
After more than 20 years of brewing, it is now official-APIs are everywhere. In a 2021 survey, 73% of companies reported that they had released more than 50...
Patches for iOS Security Wi-Fi Vulnerability Recently Announced
27th July 2021, Kathmandu
A seemingly harmless WiFi hack was recently warned to iPhone owners all around the world that it was not only potentially harmful but also a real menace. That...
How Tractable Built an AI Unicorn in 6 Years?
26th July 2021, Kathmandu
Today, the worth of Tractable is $1 billion. A leading AI company, Tractable has products that helped many of the largest P&C insurers, manufacturers, fleet owners worldwide along...
The takeover of WINDOWS DOMAINS BY New PetitPotam Attack
26th July 2021, Kathmandu
PetitPotam, the latest NTLM relay attack has been explored that allows attackers to take over a website controller, and further, a whole Windows domain.
Microsoft Active Directory Certificate Services,...
5 Steps to Amending Ransomware Resiliency
26th July 2021, Kathmandu
Alex Restrepo, the cybersecurity researcher at Veritas, lays out the key concepts that organizations should be fixating on now and implementing today.
The ransomware landscape is evolving, and ransomware...
APT Hackers Distributed Android Trojan via Syrian e-Government Portal
26th July 2021, Kathmandu
An advanced persistent threat (APT) actor has been tracked in an incipient campaign deploying Android malware via the Syrian e-Regime Web Portal, denoting an upgraded arsenal designed to...
Here’s How to Put a Secure Password on your Online Account?
25th July 2021, Kathmandu
You must have a strong password if you want to keep your online account secure. But no matter how strong the password is, it is not impossible to...
Bank Hack Threat Hackers Use US Numbers Cyber Bureau Launches Investigation
25th July 2021, Kathmandu
Bankers were panic-stricken after hackers threatened to hack the system of a bank affiliated with the Nepal Clearing House (NCHL).
The hackers have sent an email setting a deadline...
Android Malware SMS Trojans Installed through Some URL Shortened
24th July 2021, Kathmandu
Android malware and banking or SMS trojans installed through some URL shortener.
URL shortener has been very popular due to various reasons in present days which has given a...
Threat to Google Chrome Passwords: NPM Malware
24th July 2021, Kathmandu
Threat to Google Chrome Passwords: NPM Malware. NPM malware was found exploiting passwords of Google Chrome.
It is a known incontrovertible fact that organizations and individuals should protect publicly...
Google chrome and Telegram Software now have been targeted by Nasty macOS Malware XCSSET
24th July 2021, Kathmandu
Google chrome and Telegram Software now have been targeted by Nasty macOS Malware XCSSET
Malware targeting the macOS operating system has been updated again, adding more functionality to its...
Joker Billing Fraud Malware Found in Google Play Store
24th July 2021, Kathmandu
Firstly we know that Joker Malware is a Trojan Malware that secretly enters a user's device through an infected application.
The joker malware is mostly infected in apps it...
Why Using Public Wi-Fi Connections May be Dangerous?
23 July 2021, Kathmandu
With so many places in our digital world where we are vulnerably susceptible to cybercriminals assailants, perhaps at the top of the list is when we are utilizing...
Here’s a Simple Way to Understand ‘Malware’ and Protect Yourself from Malware
23 July 2021, Kathmandu
With the increasing use of the internet and digital, various means of cybercrime have started appearing. Malware is one of them. Which is becoming a challenge for everyone...
Facebook Caught Iranian Spies
23 July 2021, Kathmandu
Facebook revealed that it tracked and partly disrupted a cyber espionage campaign launched by Iranian hackers, collectively mentioned as Tortoiseshell or Imperial Kitten.
On Thursday, Facebook said that it had taken...
How Does Pegasus Software Hack Phones?
22 July 2021, Kathmandu
Pegasus software is spyware developed by an Israeli tech company called NSO Group. This group is especially known for making cyber weapons.
Pegasus is a highly sophisticated surveillance software...
Spam Terror in Messenger in the name of Honda, Don’t Open this Link by...
22 July 2021, Kathmandu
Japanese car and motorcycle maker Honda's 70th-anniversary greetings message link is currently being spread on Messenger. After clicking on the link, some rules are put along with the...
Nepal Rastra Bank Warns the Hackers Threatening Nepal’s Banking System
22 July 2021, Kathmandu
News that Nepal's banking system has been 'hacked' since Wednesday has caused panic. Mentioning the names of 16 banks, the message that the system has been "compromised" and...
Hacker Threatens to Hack NCHL Affiliated Bank System, Banker Panicked With Email
22nd July 2021, Kathmandu
Bankers have become panic-stricken after hackers threatened to hack the system of a bank affiliated with the Nepal Clearing House (NCHL).
The hackers have sent an email setting a...
Researchers Warned of Cryptojacking Attackers of Linux Operating
22 July 2021, Kathmandu
A threat group that may be located in Romania and has been active since at least 2020 has been supporting a cryptographic hijacking campaign against Linux-based machines written...
Many Critical Issues Newly Discovered in CODESYS Industrial Automation Software
21 July 2021, Kathmandu
Cybersecurity researchers on Wednesday disclosed multiple security vulnerabilities affecting the CODESYS automation software and the WAGO Programmable Logic Controller (PLC) platform. These vulnerabilities can be remotely exploited to...
How Does Cloud-Based Security Work? Cloud Computing Security
21 July 2021, Kathmandu
Cloud security is the whole bundle of technology, protocols, and best practices that bulwark cloud computing environments, applications running in the cloud, and data held in the cloud....
Mobile Device Security Best Practices You Should Know
21 July 2021, Kathmandu
These days proximately everyone has a mobile contrivance. You assuredly can’t get along in society without a perspicacious phone to avail you check scores, message your friends, make...
Ransomware Incident at Cloudstar Disrupts the Real Estate
21 July 2021, Kathmandu
A highly sophisticated ransomware incident at Cloudstar disrupts real estate. A highly sophisticated ransomware attack at Cloudstar, a cloud hosting service and managed service provider for varied real...
Sixteen Cybercriminals in Spain Who Were Behind the Grandoreiro
20th July 2021, Kathmandu
The arrest of sixteen cybercriminals in Spain who were behind the Grandoreiro and Mekotio Banking Trojan
Sixteen people who were part of a criminal network that was involved in...
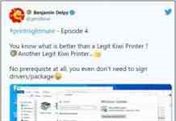
Another Unpatched Windows Printer Spooler Bug Discovered
20th July 2021, Kathmandu
After days, Microsoft was notified of an unpatched security vulnerability in the Windows Print Spooler service, yet another 0-day flaw has been identified in the same component.
Researcher Benjamin...
Status Of Cyber Forensics in Nepal, How Digital Forensics in Cyber Security Makes a...
19th July 2021, Kathmandu
Computer forensics is the application of investigation and analysis techniques to amass and preserve evidence from a particular computing contrivance in a way that is felicitous for presentation...
Google patches Chrome zero-day, eighth one in 2021
19th July 2021, Kathmandu
Eight security vulnerabilities, including a high severity zero-day flaw exploited in the wild, are inscribed by Google Chrome.
Chrome’s new version (91.0.4472.164) has been released for Windows, Mac, and...
Windows Hello Bypass Fools Biometrics Safeguards in PCs
19th July 2021, Kathmandu
An attacker to idiot a USB digital camera utilized in the biometric facial-recognition facet of the program is made possible by a Windows security bug.
A vulnerability that could...
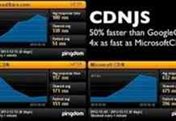
CloudFlare CDNJS Bugs Can Lead to Widespread Supply-chain Attacks
19th July 2021, Kathmandu
Critical bug discovered in Cloudflare CDNJS which could have led to supply-chain attacks. 12.7% of all the websites on the internet use the CDNJS library. Cloudflare has fixed...