Recently large-scale security breaches have highlighted a new class of threat to digital networks. Advanced Persistent Threats (APTs) have made global headlines, to the dismay of many enterprises. The most recent episode was at the Central Bank of Bangladesh, from where hackers stole millions. It is evident that the bank did not have the right protocols in place.
The Central Bank of Nepal, Nepal Rastra Bank, and even commercial banks can learn a valuable lesson from this incident, especially on what not to do. Cybersecurity experts acknowledge such types of attacks are likely. The risk is increasing for all organizations, but banks and financial institutions are at more significant risks for a simple reason—that is where the money is. Many nations recognize that the financial sector as an essential component of their critical infrastructures and economies. At the same time, this sector has been repeatedly targeted by cyber-attacks with remarkable success.
The persistence and sophistication of cyber-attacks have given rise to multiple strategic initiatives for cybersecurity in critical infrastructure protection (CIP), such as the National Institute of Standards and Technology (NIST) cybersecurity framework, information sharing programs, and other cyber strategies. Worldwide, most advanced nations have adopted similar approaches. To succeed such plan, require a high level of legal, technological, economic development, and a skilled workforce.
Unfortunately, developing nations often lack some of these competencies. Nepal needs adequate cybercrime legislation and appears to have neglected the vulnerabilities of cyber technology. The push towards government cloud systems, a supply-led approach to IT investment in Nepal, is even more dangerous given the fact that managing even the current physical network continues to remain a challenge.
Firstly, Many surveys have traditionally been conducted by private and public organizations as a means to learn about security incidents affecting several industries, Internet Service Provider, several banks and security firms publish reports describing the trends of cyber-crime incidents, threats, practitioner response strategies, and security investment decisions. Although conflict of interests in non-academic publications can be found (e.g., research to promote sales), several industry reports are considered authoritative in some regions of cybercrime). Other significant contributors are government agencies, where the financial services often rank as one of the most targeted sectors by cyber threats.
Risk Mitigation
It is the necessity to acknowledge that Nepal does not have a consistent legal framework for cybersecurity, cyber policy, and cybercrime. There is an Electronic Transaction Act (2006); however, it lacks currency concerning rapid development in the area of cybersecurity. Provided legal tribunal are not sufficient to cover all sector of cybercrime. And also the granted act is unclear to drive this critical agenda forward.
Information Security Response Team, Nepal (NPCERT.ORG), a forum for ICT security professionals, entrepreneurs and organizations in Nepal, is the only entity that has been active since 2015 in areas of cybersecurity and in raising awareness of such issues from a technical perspective, whereas in the last few months we can measure a few changes and awareness in Cyber. NPCERT has successfully organized the Global Cyber Security Summit, which we believe will bring changes in the sector of Cyber Security.
Method
This kind of learning methods focuses on the analysis of Nepalese financial services. Semi-structured interviews were conducted to allow sufficient flexibility to capture meaningful data while having enough structure to facilitate posterior comparative analysis. The goal was to explore the financial stakeholders’ experiences with security incidents, to investigate the internal and external limitations they face when handling those incidents, and then to inform strategies for improvement.
Figure1:
During the interviews, elicitation of security incidents, barriers to respondingInstitutions. 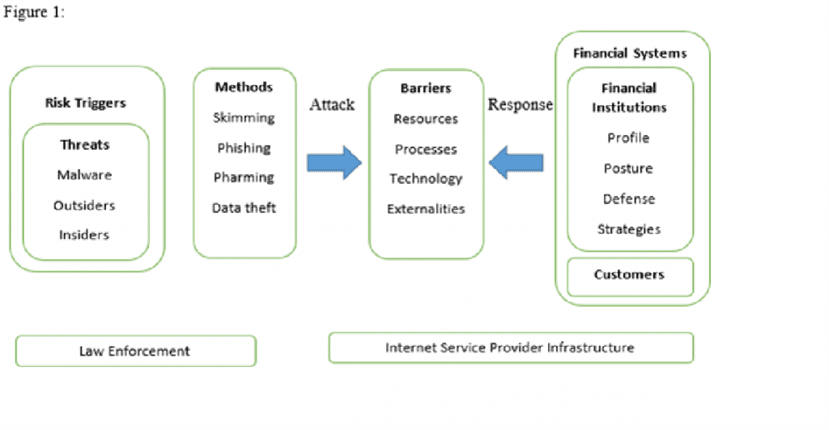

Data Collection Methods
Respondents were representatives from Banking & Insurance Sectors, government authorities with responsibilities in cybersecurity, Internet service providers (ISPs), and two CSIRTs, one supporting local business and the other supporting the national telecommunications industry. Thirty-three respondents were recruited by phone, e-mail, and in person.
When potential users declined to participate, we pursued replacements in other similar institutions.
Incidents, attitudes, and approaches.
Respondents defined ‘information security’ and ‘security incident,’ and they elaborated the distinction between an ‘incident’ and an ‘event.’ These clarifications were essential to ensure a common language during the elicitation of the frequency of incidents and concern of stakeholders. In their definitions, respondents often incorporated standard language (e.g., confidentiality, integrity, and availability) and the terms they later used to narrate their experiences during the interview (e.g., fraud).
Security Incidents
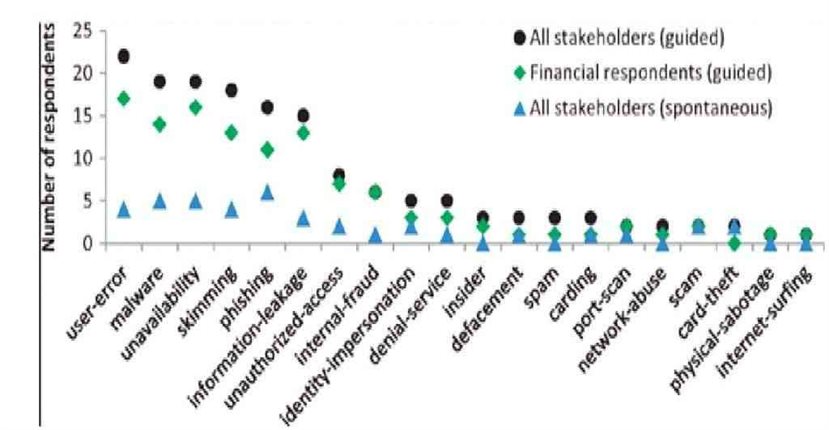
Interviewees narrated security incidents they have been experiencing over the past four years as well as consequences (unavailability and fraud). Hence, the collected data are composed of past and current occurrences at the time of the interviews. Figure 2 reveals two key findings: (i) information that respondents spontaneously reported was limited when asked about incidents, but respondents were willing to communicate additional details when asked explicitly about particular types of disturbances during guided elicitation; and (ii) there are five major incident types (and the outcome unavailability) that respondents often report, which were confirmed by authorities.

Discussion and Conclusion
The Nepalese financial services face challenging cybersecurity risks, confronts difficulties in responding to those risks appropriately (e.g., have little community security support group), and could benefit from data & information sharing as well as the creation of an NPCERT.ORG that provides and supports the adoption of strategies for better solutions. While one of the most relevant studies addressing cybersecurity in developing countries stresses that those nations marginally experience cyber-attacks, our analysis indicates that there are specific critical sectors that do gain attackers attention, and as time passes, more sophisticated attacks across borders are likely to reach domestic financial infrastructures.
While our study obtained empirical data from a diverse group of financial stakeholders across institutions and four cities in Ecuador, it does not explicitly capture the views and experiences of those institutions that declined to participate. To partially address this limitation, we included in our study the views of stakeholders (e.g., authorities) who have a broad and firsthand knowledge of incidents occurring in the financial sector and pursued replacement of potential participants from institutions of similar size.
Ultimately, insights from these tasks should contribute to improving cyber-security practice in Ecuador’s financial sector, especially if stakeholders take steps to establish a “Financial CSIRT” and a customized “information sharing program.” Future work will expand this study to identify, refine, and assess strategies that address additional elements of the barriers we have identified.
Author: Suman Thapaliya (Member of Center For Cyber Security Research & Innovation)











