Who Are Computer Hackers? Dilli Sharma
A hacker is a person who uses a computer system to gain unauthorized access to a system's data and to make the system unavailable or system down for a specific purpose...
DDoS Attack Protection And Mitigation Service Employs
Intrusion Prevention System (IPS). The Intrusion Prevention Systems (IPS) are the network security appliances that maintains the systems and networks activities for malicious acts. It is also called as Intrusion Detection and...
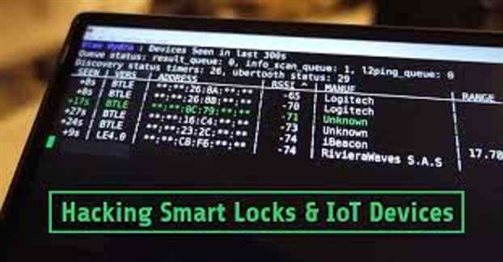
Way To Hack Smart Bluetooth Locks And IoT Devices
This might be ridiculous for someone who has invested in a cheap Bluetooth lock for their convenience, easy and quick purpose. But the attack on Bluetooth Lock was real. So let’s...
Creator of Zero-Trust Model Says Trust Did Not Exist in a Digital World
31st October 2021, Kathmandu
It appears to be no security gathering or discussion is finished without a conversation on zero trust. However, not very far in the past, "trust" was just a...
How a 12-Year-Old Path Traversal Flaw Went Unnoticed
30th October 2021, Kathmandu
Security issues and unpatched weaknesses in Wi-Fi gadgets like switches empower threat actors to invade other weak IoT gadgets in a similar organization.
An examination from security firm Tenable...
Anonymous User Leaks 500 People’s Private Information on Twitter
16th May 2020, Kathmandu
An anonymous user that goes by the username @LKhyah on Twitter has leaked data of 500 people through Twitter. The person has posted a link to Medium that...
How The Cell Phones Of Spring Breakers Who Flouted Coronavirus Warnings Were Tracked
April 06, 2020, Kathmandu
The Trump administration has focused on tracking the spread of coronavirus since its global outbreak. For this purpose, it wants to use America’s smartphone location data in order...
Live Webinar on Preventing Attacks in Google Cloud Platform
26th February 2023, Kathmandu
Get profound insights on threat hunting and incident response in Google Cloud Platform and Google Workspace infrastructure.
Join our live webinar with Sygnia's IR researchers on March 1 to...
Top 7 Cybersecurity Companies in Australia
2nd Feb 2021, Kathmandu
Cybersecurity is the practice of protecting computer systems and networks from malicious attacks. With the digital revolution and the increased reliance on computers and computer systems, cybersecurity has...
GEMS School Website Defaced By Bangladesh Hacker
4th October 2020, Kathmandu
A Bangladeshi Hacker has defaced the website of GEMS School, Lalitpur for presently unknown reasons.
The defaced website displays a page with the hacker’s alias ‘Evil Attacker’. Moreover, the...
Webinar Cum Interaction on Cyber Security Context in Nepal
May 7th, 2020, Kathmandu, Nepal
CAN Federation is organizing a series of webinars celebrating "National ICT DAY 2020". Webinar cum Interaction on "Go Digital - Stay Secure" is going to be held...
How To Remove Shortcut Virus Easily By Yourself ?
Easiest Way to Remove SHORTCUT Virus Permanently from your Computer, Pen drive, Memory Card.
In this tips and tricks is going to help you to recover your precious files that have converted...
Do VA Chatbots Need Protection? : Importance of Security
23rd November 2020, Kathmandu
VA chatbots are used in various industries for different types of assistance. They work on the concept of Machine Learning and take decisions according to it. So,...
Don’t Get Hacked! Ncell’s Expert Tips for Internet and Cyber Security
8th February 2023, Kathmandu
Recognizing the importance of internet and cyber security, Ncell has taken a bold step forward. On January 7th 2023, they released a powerful video campaign entitled "Mero Internet,...
Porn Impossible To Block In Nepal, ISPs Say
Recently, in a press statement issued by (MOCIT) Ministry of Communication and Information technology has ordered the regulator Nepal Telecommunication Authority (NTA) to ban porn websites.
As per the new Muluki Ain (Aparad Samhita) 2074,...
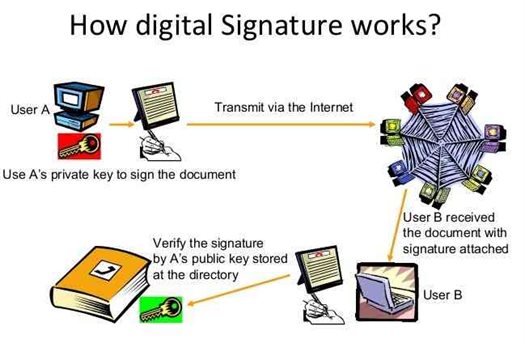
Digital Signature For Banking And Finance, Biplavman Singh
Standard Chartered procures Digital Signature from Nepal Certifying Company Pvt. Ltd
Nepal Certifying Company (NCC) penned a deal to deliver Digital Signature and Certificate (DSC) to Standard Chartered Bank Limited making it's...
Get Top Online Payment Services In Nepal, Esewa.Com.Np
Nowadays online payment is rapidly increasing day by day an increase in Information Technology. This has changed the whole world living standard. Due to the internet, this vast world has turned...
Common types of Cyber Crimes in Nepal
Cyber Crime includes illegal activities using computer or different other devices like mobile phones that are connected to a network. The numbers of Cyber Crimes has been increasing every year. The...
Global Summit On Cyber Space, A Short Report Of GCSS
Information Security Response Team Nepal (NPCERT) is a group of cybersecurity professionals in Nepal to address the urgent need for the protection of information. It is carrying various cybersecurity events within...
Nintendo Data Breach Tally Reaches 300,000
June 11, 2020, Kathmandu
On April 24th, Nintendo confirmed a hack of over 160,000 gamers’ accounts as hackers exploited the Nintendo Network ID (NNID) login system. The Japanese video game giant stated...
The takeover of WINDOWS DOMAINS BY New PetitPotam Attack
26th July 2021, Kathmandu
PetitPotam, the latest NTLM relay attack has been explored that allows attackers to take over a website controller, and further, a whole Windows domain.
Microsoft Active Directory Certificate Services,...
Hackers Taste Bitterness Of Their Medicine, Darknet MarketPlace Swarmshop Hacked
11th April 2021, Kathmandu
Until recently, the carding store Swarmshop was a popular, illicit online market where cybercriminals could go to sell and purchase stolen credit cards and banking data. However, the...
How To Use DSC For The First Time In Your PC ?
Steps for Using Token from Nepal Certifying Company
Insert the provided token and wait for the dialogue box to appear.
Click on the Open folders to view files, three directories Mac/Linux/Windows will be displayed.
...
Nepal to Host National Cyber Security Policy Stakeholder Consultation
6th June 2021, Kathmandu
National cybersecurity policy stakeholder consultation is going to be held on 6th June 2021 from 4 PM. The multistakeholder webinar is organized by the Internet Governance Institute in...
Webinar of Redefining the Role of CISOs in the Digital Transformation Era
21st January 2022, Kathmandu
In today’s digitally transformed era, tech-driven innovations that were once progressive have now become a standard practice for remaining in business.
Executing a digital transformation at the speed of...
How to Run Google SERP API Without Constantly Changing Proxy Servers
1st November 2020, Kathmandu
Scraping Google search results can become a hassle, and you've probably run into a severe problem when trying to try to do so.
You might be changing prox servers...
Security And Privacy Issues In E-Government, Pavan Duggal
Mr. Pavan Duggal is the President from India has been working on Cyberlaw Asia.Net on Security Issues of E-Government Applications. He is the pioneering of Cyberlaw and the Director of the...
Cybersecurity Awareness Training: Securing The Cyber World
28th Cyber Security Training has been successfully conducted at Peacezone Hostel, Laliguras Chowk, Bharatpur municipality-7, Chitwan, Nepal.
August 08, 2016 - The program was conducted and coordination in the initiation of the...
‘Supply Chain Attack’ on 35 Big Companies including Microsoft, Apple, PayPal
13th Feb 2021, Kathmandu
An ethical hacker (researcher) has recently shown a novel supply chain attack. As a result, the networks of more than 35 major technology companies such as Microsoft, Apple,...
Emerging Cybersecurity Technologies to Know for 2022
Technology is continually developing and presently, like never before, remaining in front of the computerized advancement – explicitly online protection – is essential to an association's prosperity.
This previous year, we have...