Telegram Platform Abused in ‘ToxicEye’ Malware Campaigns
23rd April 2021, Kathmandu
Hackers are leveraging the popular Telegram messaging app by embedding its code inside a remote access trojan (RAT) dubbed ToxicEye, new research has found. A victim’s computer infected...
Sixteen Cybercriminals in Spain Who Were Behind the Grandoreiro
20th July 2021, Kathmandu
The arrest of sixteen cybercriminals in Spain who were behind the Grandoreiro and Mekotio Banking Trojan
Sixteen people who were part of a criminal network that was involved in...
Which Physical Security Measure Is In Place ?
You are testing physical security measures as part of a pen test team. Upon entering the lobby of the building, you see the entrance has a guard posted at the lone...
Hackers from China implanted PlugX Variant on MS Exchange Servers
29th July 2021, Kathmandu
Hackers from China implanted PlugX Variant on MS Exchange Servers after Compromise. A Chinese cyberespionage organization targeting Southeast Asia took advantage of a vulnerability in the Microsoft Exchange...
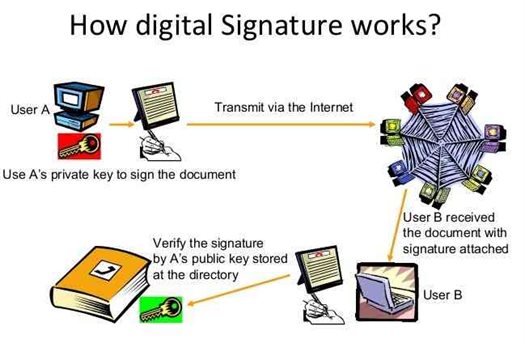
Digital Signatures Simplified For Consumers And Businesses
A digital signature is an encoded form of a message, which is used to validate digital information such as e-mail messages, PDF documents by the sender or the sign holder and...
Pokhara University Computer Hacked Dramatically
The computer of Pokhara University exam department has been hacked dramatically. The person who was supposed to measure the furniture hacked the network that includes thousands of student's data.
The incident occurred...
Is DSC Helps To Regulate E-payment Gateway In Nepal ?
Is Digital Signature & Certificate (DSC) helps to regulate the e-payment gateway in Nepal?
A digital signature is a government-sanctioned unique identification code, which is used to validate digital information such as...
SheIn Data Breach Leaked Personal Details 6.4 Million Customers To Hackers
From last few time back different governmental and nongovernmental sites has been hacked or attacked throughout the world. Information about data breach has become a widespread issue. Day by the incident...
Cyber Security Bootcamp and Training Conducted Successfully At Pokhara
September 4th, 2019
A training on ‘Cyber Security - Securing Business in the 21st Century was organized by Annapurna Software Development in association with One Cover Private Limited at Hotel Barahi Pokhara...
Security Startup Verkada’s Surveillance Cameras at Tesla
13th April 2021, Kathmandu
Security Startup Verkada's Surveillance Cameras at Tesla, Hundreds of More Businesses Breached
A small group of hackers viewed live and archived surveillance footage from hundreds of businesses including Tesla...
Researchers Detail Modus Operandi of Shiny Hunters Cyber Crime Group
25th August 2021, Kathmandu
ShinyHunters, a notorious cybercriminal underground group that's been on a knowledge breach spree since last year, has been optically canvassed probing companies' GitHub repository ASCII text file for susceptibilities which will be abused to...
How To Make Your Facebook Account More Secure ?
Facebook is the largest online social network in the world. To use it more securely we must have to clear view of the security and privacy settings.
Here are the points that...
How To Use DSC For The First Time In Your PC ?
Steps for Using Token from Nepal Certifying Company
Insert the provided token and wait for the dialogue box to appear.
Click on the Open folders to view files, three directories Mac/Linux/Windows will be displayed.
...
Common types of Cyber Crimes in Nepal
Cyber Crime includes illegal activities using computer or different other devices like mobile phones that are connected to a network. The numbers of Cyber Crimes has been increasing every year. The...
How to Use your iPhone or iPad to Scan Documents?
12th November 2021, Kathmandu
You might not realize it, but your iPhone, iPad, and iPod touch all feature a built-in scanner that lets you scan and send documents without the need for...
Web Application Security Measures, Ashok Gurung
28h June 2020, Kathmandu
Web application security is one major component in web application development that often gets overlooked.
Let's get a better insight into the cybersecurity sector from the executive member at...
How Does DMARC Avert Phishing?
29th September 2021, Kathmandu
DMARC is an ecumenical standard for email authentication. It sanctions senders to verify that the electronic mail genuinely emanates from whom it claims to emanate. This avails curb...
WhatsApp Photo Filter Bug Could Have Exposed Your Data to Remote Attackers
4th September 2021, Kathmandu
A now-patched high-astringency security susceptibility in WhatApp's image filter feature could have been abused to send a malignant image over the messaging app to read sensitive information from...
Publicity around the hack of Mr. Zuckerberg’s accounts
People, not computers, create computer threats. Computer hackers are unauthorized users who break into PC systems to steal, change or destroy the information and data. Anyone who uses a computer connected...
Cyber Security Awareness program Offered CyberSafe In School
CYBER SECURITY AWARENESS PROGRAM: DATE: 25th June 2016
Cyber Security is the most discussed issue in the world today. The ever increasing technological risk needs to be known and identified by those who...
The Top 10 Highest Paying Jobs In Information Security Domain
The organizations are doubling their demands for talented and qualified security professional since the concerns about hacking, data security, and privacy; identity thefts are increasing these days with many high-profile data breaches...
Career Path in Cyber Security Webinar Successfully Conducted
22nd May 2021, Kathmandu
A one-day event was organized virtually by npCert, CSRI Nepal in association with Texas College of Management and IT with the title 'Career Path in Cyber Security on...
Internet Communication Security Counter measurers
A wide variety of countermeasures are needed to protect an organization from the assortment of threats. The counter measure's used to defend Internet-based threats are not much different from those protecting...
Gigaset Android Phones Infected By Malware By Hacked Update Server
10th April 2021, Kathmandu
Gigaset, a German multinational company well known in the area of communication revealed to have a malware infection in their android phones. Owners of Gigaset android phones have...
Why Content Scrambling System (CSS) ?
The way of scrambling computer data is called encryption so it can only be read by authorized people. It is one of the best means of securing data over the internet....
User’s not Accepting Privacy terms to face Limited Functionality: WhatsApp
19th May 2021, Kathmandu
What’s App has removed the May 15th finishing date for accepting the new privacy policy. In fact, the social messaging app now says the user will not lose...
Is Facial Recognition Secure on Smartphones and Should You Use It?
10th November 2021, Kathmandu
Face unlocking technology is not the same on all smartphones; some are more secure than others. This is why.
Facial recognition is becoming more widespread on personal devices such...
Microsoft Launches a National Campaign to Support Community Colleges in their Efforts to Grow...
31st October 2021, Kathmandu
The United States is facing a cybersecurity skills shortage: Microsoft has launched a national campaign to support community colleges in their efforts to grow their cybersecurity workforce.
The last...
Modern Laptops Are Vulnerable To Cyber Attacks- Experts
When we buy laptops or computers, we only look after its version, Storage and other technical aspects but never think about its capacity to provide security for our sensitive files and...
Cybercriminals Make Twitter a Playing Field to Target Indonesian Banks
6th April 2021, Kathmandu
In recent years, cyberattacks have been increasing day by day. Nowadays, Cybercriminals have placed more pressure on the financial sector. A recent study shows that 65 % of...