Bandidos, a Spying Campaign in Latin America Discovered
13th July 2021, Kathmandu
An active malicious campaign that utilizes a new version of old malware, Bandook; syping on victims discovered by ESET researchers.
An ongoing campaign targeting corporates networks at Venezeula was detected. When comparing the malware utilized in this campaign with what was previously documented, new functionality and new changes to the present malware, referred to as Bandook, were found. Researchers have found that the campaign targeting Venezuela, despite being active since a minimum of 2015, has somehow remained unrecorded. Researchers called this campaign Bandidos, given the malware used and since targeted the locale.
What is Bandook?
Bandook is an old remote access trojan: there are references thereto being available online as early as 2005, though its use by organized groups wasn’t documented until 2016. The report published that year by EFF, Operation Manual, describes the utilization of Bandook to focus on journalists and dissidents in Europe. Then in 2018, Lookout published its research uncovering other espionage campaigns that had different targets but used an equivalent infrastructure. They gave the name Dark Caracal to the group liable for the attacks. Finally, Check Point’s report in 2020 showed that the attackers began to use signed executables to focus on many verticals in various countries.
Previous reports have mentioned that the developers of Bandook could be developers for hire (also referred to as “malware as a service”), which is sensible given the varied campaigns with different targets seen through the years. We must note, however, that in 2021 we’ve seen just one active campaign: the one targeting Spanish-speaking countries that we document here.
Although we’ve seen quite 200 detections for the malware droppers in Venezuela in 2021, we’ve not identified a selected vertical targeted by this malicious campaign. According to our telemetry data, the most interests of the attackers are corporate networks in Venezuela; some in manufacturing companies, others in construction, healthcare, software services, and even retail. Given the capabilities of the malware and therefore the quiet information that’s exfiltrated, it looks like the most purpose of those Bandidos is to spy on their victims. Their targets and their method of approaching them are more almost like cybercrime operations than APT activities like Operation Manual.
How does it Operate:
The victim sectors are mostly construction, manufacturing, healthcare, and retail.
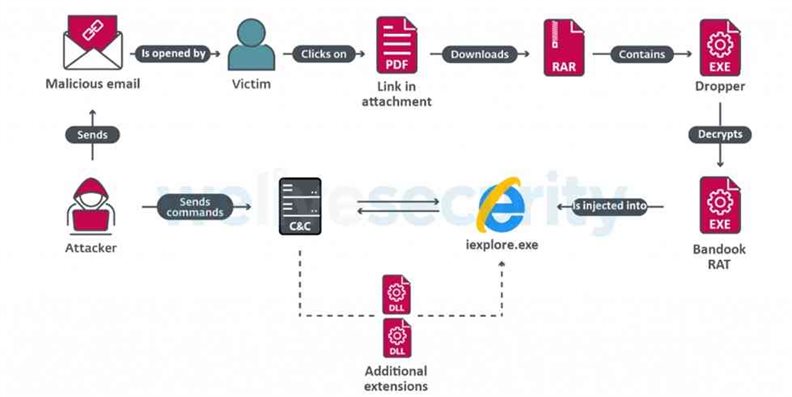
The attack bond begins with victims getting malicious emails with PDF attachments having shortened URLs, Redbrandly, or Bitly. The PDF file contains a link to download a compressed archive and therefore the password to extract it, hosted on SpiderOak, iCloud, and Google Cloud. Inside the archive, there’s an executable file: a dropper that injects Bandook into an online Explorer Process.
The latest of Bandook variants is available with 132 commands, 120 higher than the previously documented variant. This signifies that the attackers have improved the malware capabilities.
The main commands contain listing directory contents, taking screenshots, controlling the cursor on the infected machines, manipulating files, installing malicious DLLs, and others.
A new interesting feature of this malware is ChromeInject functionality. This goes for stealing the victims’ credentials. Once the communication with the C2 server is developed, the payload downloads a DLL file, which creates a malicious Chrome extension.
Then the malicious Chrome extension tries to obtain any credentials on the victims and storing them into Chrome’s local storage.
The figure below shows a summary of the attack chain:
Figure 1 from ESET on attack overview
The figure below shows that the email containing the attachments are usually short.
 The two figures 3 and 4 given below are the examples of PDF used in this campaign, those are, actually stock images available online.
The two figures 3 and 4 given below are the examples of PDF used in this campaign, those are, actually stock images available online.

 The PDF files have been used with different filenames that change between targets and the password for downloading the archive is 123456.
The PDF files have been used with different filenames that change between targets and the password for downloading the archive is 123456.
Conclusion:
Book, a RAT active since 2005 has its involvement in different espionage campaigns, already documented proves that it is still a relevant tool for cybercriminals. Also, considering the modification made to malware over the years signifies the keen interest of cybercriminals to keep using this piece of malware in the future. That’s why, protection against such threats should be done by organizations for which, updating and reviewing their security postures is recommended.