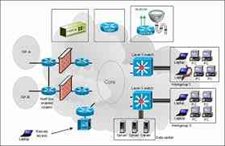
Enterprise Network Security relates to the real-time defense and preventive measures implemented by an enterprise to protect the business network and threats that may breach or paralyze the network system. This security method helps to preserve the business sensitive information and applications from falling into the wrong hands with the help of software, hardware, and IT strategies.
An organization needs to protect the malicious approach for it’s the business network to function correctly and effectively. The data and information n transmitted and received over a network without any protection can fall into the wrong hands and attacks such as spyware, Trojan horses, phishing, exploitation of vendor-specific vulnerabilities and self-propagating worms.
These attacks can lead to slow processing of network traffic into bottlenecks, hinder connectivity and may damage severely that it could crash an entire system. Thus the enterprise network security provides the preventative real-time protection that needs to be highly confidential. This security can also protect the system using anti-virus software and firewall but only with the help of system analysis practices and thus prevent the attacks before they cause service disruptions.
There are a few ways that the Enterprise Network Security protects network security. These methods are illustrated as:
As a sensor, the network system gives the deep and wide imperceptibility into unusual traffic patterns, unknown devices, unusual movement designs, and unexpected behavior and with Cisco IOS Net Flow. Thus the network can now distinguish the undetected, proactively.
As an enforcer, the network may contain an attack with Cisco TrustSec by authorizing segmentation and user access control. Thus when the attackers get inside their entrance is limited into just one portion of the system.
As a mitigation accelerator, the network may remediate breaches through computerization with the Cisco Application Policy Infrastructure Controller Enterprise Module (APIC). So instead of network remediation and mitigation box by box over time of weeks or months, the organization can apply it in near time throughout the entire organization.