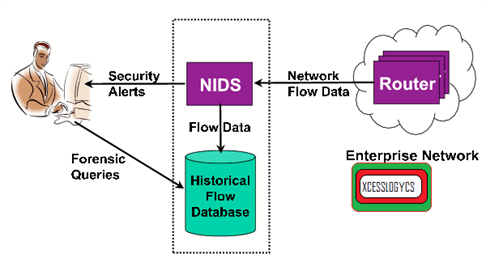
The Intrusion Detection System (IDS) is a software application or a device that monitors system or network activities for policy violation or malicious activities and gives electronic reports to the management department.
The Intrusion Detection System comes in different forms and reaches the objective of detecting suspicious traffic in various ways. There are Host Based Intrusion Detection Systems (HIDS) and Network Based Intrusion Detection Systems (NIDS). The NIDS is a network security system that focuses on the attacks that enter from the internal source of the network via authorized users.
Various systems might try to stop an intrusion process; however, this is neither expected nor required from a monitoring body. Intrusion Detection and Prevention System (IDPS) are mainly dedicated to detecting the possible incidents, reporting attempts and logging information about them. Many organizations access IDPSs for other interests like identifying problems with security issues, deterring personnel from violating security policies and documenting existing threats. IDPSes have now become an essential addition to every organizations’ security infrastructure.
Generally, the IDPSes record data and information regarding observed events alerts security administrators of essential observed events and submit reports. Several IDPs also take action to a threat that is detected by trying to stop it from becoming successful.
They use appropriate technologies that include the IDPS preventing the attack on its own thereby changing the attack’s content and changing the security environment such as reconfiguring of a firewall.
An IDS that is duly based that will maintain the network traffic and compare it with a baseline which is already established is referred to Statistical anomaly-based IDS whereas a signature-based IDS supports packets on the network and compare it with a database of attributes or signature from the recognized malicious threats.