Cybercrime Group Lazarus Upgrades Its Arsenal With VYVEVA Malware
11th April 2021, Kathmandu
Lazarus Group is a cybercrime group made up of an unknown number of individuals. The United States Federal Bureau of Investigation says that the Lazarus Group is a North Korean “state-sponsored hacking organization”. It has often targeted global companies with new malware strains such as AppleJeus, Fileless, ThreatNeedle, and MATA.
On Thursday, ESET (Essential Security against Evolving Threats, a Slovak internet security company that offers antivirus and firewall products) said the new backdoor malware, dubbed Vyveva, was traced in an attack against a South African freight and logistics firm.
Dubbed Vyveva, the malware is capable of performing certain backdoor functionalities like exfiltrating files, harvesting information from an infected system, and running arbitrary code by remotely connecting to a command-and-control (C2) server. Vyveva is one of the latest weapons discovered in the Lazarus arsenal. Vyveva was first used in a June 2020 attack as ESET researchers discovered, but further evidence shows Lazarus has been deploying it in previous attacks going back to at least December 2018.
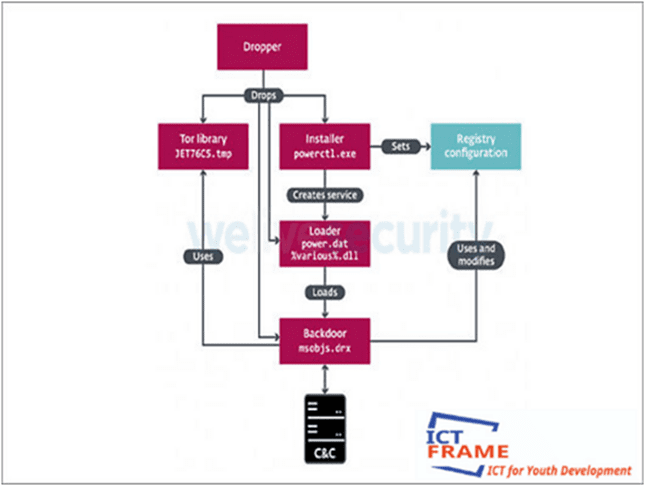
Vyveya’s Components
Up until now, we have managed to find three of the multiple components comprising Vyveva – its installer, loader, and backdoor. The installer is the earliest chronological stage found and since it expects other components to be already present on the machine, it suggests the existence of an earlier, unknown stage – a dropper. The loader serves to decrypt the backdoor using a simple XOR decryption algorithm.