These are the Common Forms of Web Application Attacks
6th October 2021, Kathmandu
There has been a remarkable ascent in the number of organizations accepting computerized changes like web applications to smooth out their responsibility and carefully trade information and exchanges. While this has various advantages for clients, it likewise features critical shortcomings and weaknesses in internet browsers that lead to web application assaults. You can try not to succumb to information breaks and other such assaults by being knowledgeable in relieving the danger of web applications assaults.
It would likewise assist with thinking about the most famous electronic assaults to fabricate a procedure to relieve such dangers.
Powerless validation is a situation where the layers of safety are more fragile or incongruent with the worth of ensured resources. Besides, powerless confirmation can likewise point towards a circumstance where the verification interaction is imperfect or helpless.
Then again, a Cross-Site Request Forgery or Session Riding assault can upset the activity between the business and the client. The assailant uses social designing methods to fool the objective into executing a manufactured solicitation in their server. Henceforth, it becomes unimaginable for the client to recognize what’s genuine and so forth. Subsequently, it prompts problematic electronic assaults.
Since access control plan choices are made by people and not machines, the extent of mistakes sneaking in through feeble access controls is somewhat high. Thus, assailants rapidly clear their path through a web application assault and break the availability and protection of the put-away information in the event of powerless access controls.
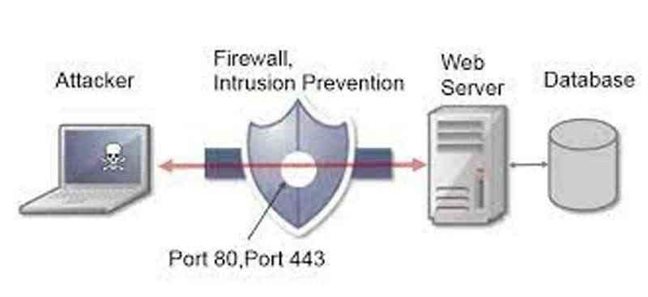
Further, assailants can meddle with an application’s inquiry to its data set through a SQL assault. Through this, they can get information inaccessible to them in ordinary conditions and hazard protection and the legitimacy of the information.
To guide away from these web application assaults, you should have total permeability of the code being run on your site and lead normal security evaluations. Web Application Hacking and Security (WAHS) Course is created by the very group that fostered the C|EH to give you involved preparing in a lab-based climate.
Support yourself to battle against the highest online assaults through a directed dominance course at EC-Council. Become a Certified Web Application Security Professional today.