Apple’s Plan to Scan Your Phone’s Images
20th October 2021, Kathmandu
Apple’s arrangement to filter clients’ telephones and different gadgets for pictures portraying youngster sexual maltreatment created a reaction over protection concerns, which drove the organization to report a postponement.
Apple, Facebook, Google, and different organizations have since quite a while ago examined clients’ pictures that are put away on the organizations’ servers for this material. Examining information on clients’ gadgets is a critical change.
Anyway benevolent, and regardless of whether Apple is willing and ready to finish its vows to ensure clients’ security, the organization’s arrangement features the way that individuals who purchase iPhones are not bosses of their own gadgets. Also, Apple is utilizing a confounded examining framework that is difficult to review. In this way, clients face an obvious reality: If you utilize an iPhone, you need to trust Apple.
In particular, clients are compelled to trust Apple to just utilize this framework as depicted, run the framework safely over the long haul, and put the interests of their clients over the interests of different gatherings, remembering the most impressive stats for the planet.
Notwithstanding Apple’s so-far-exceptional arrangement, the issue of trust isn’t explicit to Apple. Other huge tech organizations likewise have impressive authority over clients’ gadgets and knowledge of their information.
What Is Trust?
Trust is “the readiness of a party to be powerless against the activities of another party,” as per social researchers. Individuals base the choice to trust on experience, signs, and signals. Yet, past conduct, guarantees, the manner in which somebody acts, proof, and even agreements just give you information focuses. They can’t ensure future activity.
Consequently, trust involves probabilities. You are, one might say, moving the dice at whatever point you trust somebody or an association.
Reliability is a secret property. Individuals gather data about somebody’s reasonable future conduct, yet can’t know without a doubt whether the individual can adhere to their promise, is genuinely altruistic, and has the honesty – standards, cycles, and consistency – to keep up with their conduct after some time, under tension or when the surprising happens.
Trust in Apple and Big Tech
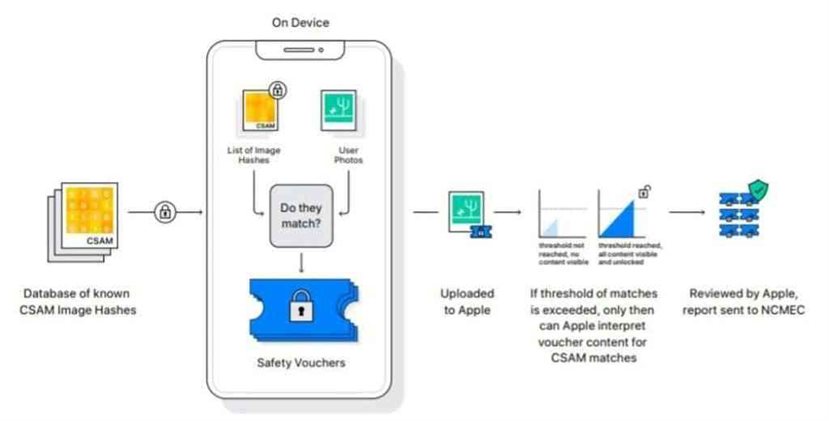
Apple has expressed that its checking framework will just at any point be utilized for distinguishing kid sexual maltreatment material and has numerous solid security insurances. The specialized subtleties of the framework show that Apple has found a way ways to secure client protection except if the designated material is distinguished by the framework.
For instance, people will audit somebody’s presume material just when the occasions the framework distinguishes the designated material arrives at a specific limit. Nonetheless, Apple has given minimal verification in regards to how this framework will function practically speaking.
Apple’s new framework for contrasting your photographs and a data set of known pictures of kid misuse works on your gadget instead of on a server.
In the wake of examining the “NeuralHash” calculation that Apple is putting together its filtering framework with respect to, security scientists and social liberties associations caution that the framework is probable helpless against programmers, rather than Apple’s cases.
Pundits additionally dread that the framework will be utilized to filter for other material, like signs of political difference. Apple, alongside other Big Tech players, has buckled under the requests of tyrant systems, strikingly China, to permit government observation of innovation clients. Practically speaking, the Chinese government approaches all client information. What will be distinctive this time?
It ought to likewise be noticed that Apple isn’t working on this framework all alone. In the U.S., Apple intends to utilize information from, and report presume material to, the not-for-profit National Center for Missing and Exploited Children. Accordingly, believing Apple isn’t sufficient. Clients should likewise trust the organization’s accomplices to act kindheartedly and with trustworthiness.
Big Tech’s Less-Than-Encouraging Track Record
This case exists inside a set of customary Big Tech protection attacks and moves to additionally shorten shopper opportunities and control. The organization’s host situated themselves as mindful gatherings, however, numerous protection specialists say there is too little straightforwardness and insufficient specialized or chronicled proof for these cases.
Another worry is unseen side-effects. Apple may truly need to secure youngsters and ensure clients’ protection simultaneously. All things considered, the organization has now reported – and marked its dependability to – an innovation that is appropriate to keep an eye on huge quantities of individuals. States may pass laws to stretch out examining to other material considered illicit.
Would Apple, and possibly other tech firms, decide to not observe these laws and conceivably pull out of these business sectors, or would they agree with possibly draconian neighborhood laws? Who knows about the future, however, Apple and other tech firms have decided to assent to harsh systems previously. Tech organizations that decide to work in China are compelled to submit to oversight, for instance.
Weighing Whether to Trust Apple or Other Tech Companies
There’s no single response to whether or not Apple, Google, or their rivals can be trusted. Dangers are diverse relying upon what your identity is and where you are on the planet. An extremist in India faces various dangers and dangers than an Italian safeguard legal counselor. Trust involves probabilities, and dangers are probabilistic as well as situational.
It’s a question of what likelihood of disappointment or double-dealing you can live with, what the pertinent dangers and dangers are, and what securities or alleviations exist.
Your administration’s position, the presence of solid neighborhood protection laws, the strength of law and order, and your own specialized capacity are applicable elements. However, there is one thing you can rely on: Tech firms regularly have broad command over your gadgets and information.
Like every single enormous association, tech firms are complicated:
Employees and the executives go back and forth, and guidelines, approaches, and force elements change.
An organization may be dependable today yet not tomorrow.
Enormous Tech has shown practices in the past that should make clients question their reliability, specifically with regards to protection infringement. Yet, they have additionally protected client security in different cases, for instance in the San Bernadino mass shooting case and ensuing discussions about encryption.
To wrap things up, Big Tech doesn’t exist in a vacuum and isn’t almighty. Apple, Google, Microsoft, Amazon, Facebook, and others need to react to different outer tensions and forces. Maybe, thinking about these conditions, more noteworthy straightforwardness, more autonomous reviews by columnists and confided in individuals in common society, more client control, more open-source code and real talk with clients may be a decent begin to adjust various goals.
While just an initial step, customers would basically have the option to settle on more educated decisions regarding what items to utilize or purchase.