Chinese Spyware Being Used in Widespread Cyber Espionage Attacks
4th August 2021, Kathmandu
A threat actor surmised to be of Chinese inception has been linked to a series of 10 attacks targeting Mongolia, Russia, Belarus, Canada, and the U.S. from January to July 2021 that involve the deployment of a foreign access trojan (RAT) on infected systems, consistent with incipient research.
The intrusions are attributed to a complicated assiduous threat denominated APT31 (FireEye), which is tracked by the cybersecurity community under the monikers Zirconium (Microsoft), Judgement Panda (CrowdStrike), and Bronze Vinewood (Secureworks).
The group may be a “China-nexus cyber espionage actor fixated on obtaining information which will provide the Chinese regime and verbalize-owned enterprises with political, economic, and military advantages,” consistent with FireEye.
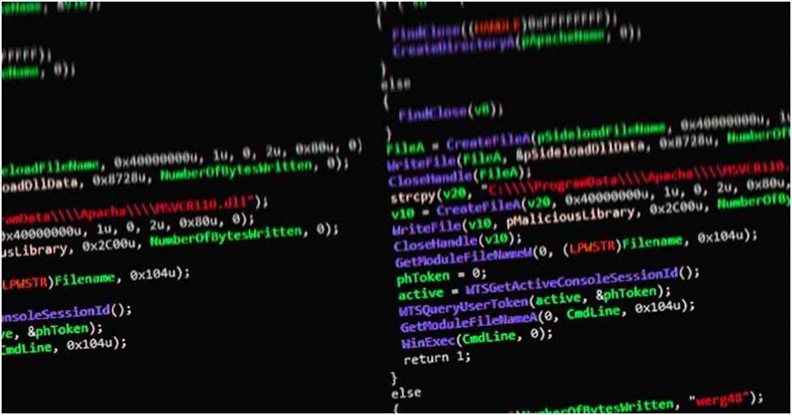
Positive Technologies, during an indite-up published Tuesday, revealed an incipient malware dropper that was habituated to facilitate the assailants, including the retrieval of next-stage encrypted payloads from a foreign command-and-control server, which is subsequently decoded to execute the backdoor.
The malevolent code comes with the capacity to download other malware, potentially putting affected victims at further peril, also as perform file operations, exfiltrate sensitive data, and even efface itself from the compromised machine.
“The code for processing the [self-expunge] command is categorically intriguing: all the engendered files and registry keys are expunged utilizing a bat-file,” Positive Technologies researchers Denis Kuvshinov and Daniil Koloskov verbalized.
Withal deserve particular note is that the malware’s homogeneous attributes thereto of a trojan designated DropboxAES RAT that was put to utilize by an equivalent threat group last year and relied on Dropbox for its command-and-control (C2) communications, with numerous overlaps found within the techniques and mechanisms wont to inject the assailment code, achieve sedulousness, and therefore the mechanism employed to expunge the espionage implement.
“The revealed homogeneous attributes with earlier versions of maleficent samples described by researchers, like in 2020, suggest that the group is expanding the geography of its intrigues to countries where its growing activity are often detected, Russia especially ,” the researchers concluded.