What Is Digital Signature And How Does It Work ?
As Digital Marketing is in high demand the secureness and confidentiality of each data and message are the significant part to be kept secure and confidential from an eavesdropper. Today many competitive organizations are hiring hacker and security experts to secure their data from a spammer and in need of knowing other competitive organizations info. So secureness and privacy are the essential factors for any government to banking organization to be protected from the hacker.
For this in the modern time, public key encryption technology also known as Digital Signature is the essential technique utilized to secure any confidential data and messages such as username and password of each. So, Digital Signature is the most advanced and secured type of electronic signature mathematically used to validate the authenticity and integrity of a message, electronically or digitally in digital communication.
Digital Signature uses a standard, accepted format called Public Key Infrastructure (PKI) to provide the highest level of security and universal acceptance for certifying the authenticity of the signature. Furthermore, Digital Signatures use a certificate-based digital ID issued by an accredited Certifying Authority (CA) or Trust Service Provider (TSP) to secure data and message.
How does Digital Signature work?
Digital Signature is asymmetric cryptography that uses a public key algorithm such as RSA to authenticate digital information such as e-mail messages, electronic documents or macros. Furthermore, it uses two keys, a public key known to everyone and a private key, the most secured key only known to the principal owner. So, just the public key is used to encrypt the plaintext messages into ciphertext and only the corresponding private key is used to decrypt the ciphertext, i.e., encrypted message to plain text.
To create a digital signature, a signer electronically signs a document, and the name is generated using the signer’s private key for securing the paper by the signer. Then the mathematical algorithm called cipher used to create a signed document called a hash and encrypting that data. So the outcoming encrypted information is the digital signature. If the document changes after signing a paper, it is invalidated otherwise it is validated.
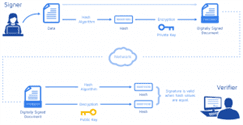
For example, Achyut signs an agreement to sell a timeshare using his private key. The buyer who receives the data also gets a copy of Achyut’s public key. If the send public key can’t decrypt the signature, it means the name is not of Achyut’s or may change as time passes. So the signature is considered to be invalid. For this reason, PKI requires the keys to be created, conducted and saved confidentially for the requirement of safe and secured digital signing procedure.
Furthermore digital Signature also guarantees Authenticity, Integrity, Non-repudiation, and Notarization. To make these assurances, following criteria fulfilled:
- The digital signature is valid
- The certificate is to be current, not expired.
- The publisher, i.e., the signing person or organization is to be trusted.
- Through a reputable certificate authority (CA), the certificate is to issue to the signing publisher.







