Can Computer Security Deliver Business Value?
Information Technology security sometimes called as computer security is the information security that is applied to technology which most often relates to the same form of computer system, but it is necessary to know that the computer does not always mean a desktop computer at home. A network may be termed as an electronic device with a processor, and that has got some storage. These devices may be simple non-networked standalone devices such as calculators to large networked mobile computing devices such as smartphones to the tablet pcs.
The IT security specialists are almost probable to be found in any large establishment or enterprise as according to the nature of data within larger businesses. They are lone responsible for providing security to all the technology within the organization from malicious cyber attack that sometimes tries to breach into vulnerable while equally confidential private information or have access to the internal systems.
The importance of IT security has driven societies to develop innovative methods of protecting their data. For example, the Roman Empire’s military wrote sensitive messages on parchments that could be dissolved in water after they had been read by the authority. Military history provides another more recent example of the importance of information security.
After decades as World War II ended, it was revealed that the Allies had gained a considerable advantage by translating both the Japanese and German encryption codes early in the war. Recent innovations in information technology like the Internet have made it possible to send a massive amount of data across the world conveniently. But the task of controlling and protecting that information has grown exponentially now that data can be easily copied, manipulated, transmitted, manipulated, stored and destroyed.
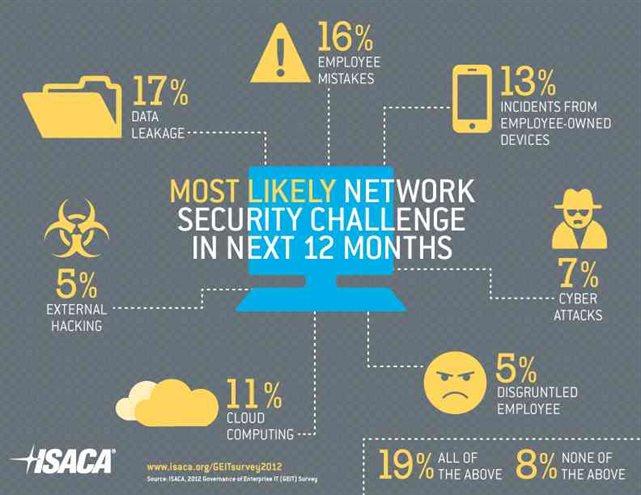
Information technology security sometimes refers to the challenge of balancing the demands of users versus the need for data integrity and confidentiality. For example, allowing employees to access a network from a remote location like their home or a project site can increase the value of the net and efficiency of the employee. But remote access to a system also opens some vulnerabilities, loopholes and makes difficult security challenges for a network administrator.