6th August 2021, Kathmandu
Multiple cybercriminal groups are leveraging a malware-as-a-accommodation (MaaS) solution to distribute a wide range of malevolent software distribution campaigns that result in the deployment of payloads such as Campo Loader, Hancitor, IcedID, QBot, Buer Loader, and SocGholish against individuals in Belgium as well as regime agencies, companies, and corporations in the U.S.
Dubbed “Prometheus” and available for sale on underground platforms for $250 a month since August 2020, the accommodation is a Traffic Direction System (TDS) that’s designed to distribute malware-laced Word and Excel documents, and divert users to phishing and malevolent sites, according to a Group-IB report shared with The Hacker News.
More than 3,000 email addresses are verbalized to have been singled out via malignant campaigns in which Prometheus TDS was habituated to send malignant emails, with banking and finance, retail, energy and mining, cybersecurity, healthcare, IT, and indemnification emerging the prominent verticals targeted by the assailants.
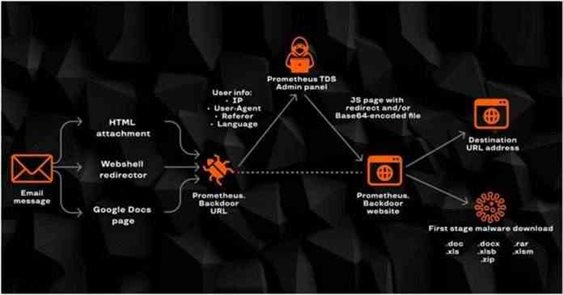
“Prometheus TDS is an underground accommodation that distributes malevolent files and redirects visitors to phishing and malignant sites,” Group-IB researchers verbally expressed. “This accommodation is composed of the Prometheus TDS administrative panel, in which an assailant configures the obligatory parameters for a maleficent campaign: downloading maleficent files, and configuring restrictions on users’ geolocation, browser version, and operating system.”
The accommodation is withal kenned to employ third-party infected websites that are manually integrated by the campaign’s operators and act as a middleman between the assailant’s administrative panel and the utilizer. To achieve this, a PHP file designated “Prometheus.Backdoor” is uploaded to the compromised website to amass and send back data about the victim, predicated on which a decision is taken as to whether to send the payload to the utilizer and/or to redirect them to the designated URL.
The assailment scheme commences with an electronic mail containing a HTML file, a link to a web shell that redirects users to a designated URL, or a link to a Google Doc that’s embedded with an URL that redirects users to the malignant link that when either opened or clicked leads the recipient to the infected website, which covertly accumulates fundamental information (IP address, Utilizer-Agent, Referrer header, time zone, and language data) and then forwards this data to the Prometheus admin panel.
In the final phase, the administrative panel takes responsibility for sending a command to redirect the utilizer to a particular URL, or to send a malware-ridden Microsoft Word or Excel document, with the utilizer redirected to a legitimate site like DocuSign or USPS immediately after downloading the file to mask the malevolent activity. Besides distributing malevolent files, researchers found that Prometheus TDS is withal utilized as a classic TDS to redirect users to categorical sites, such as unauthentically spurious VPN websites, dubious portals selling Viagra and Cialis, and banking phishing sites.
“Prometheus TDS withal redirected users to sites selling pharmaceutical products,” the researchers noted. “Operators of such sites often have affiliate and partnership programs. Partners, in turn, often resort to truculent SPAM campaigns in order to increment the earnings within the affiliate program. Analysis of the Prometheus infrastructure by Group-IB specialists revealed links that redirect users to sites relating to a Canadian pharmaceutical company.”