Building Secure Data Access,Threats And Countermeasures
The network security contains the policies taken to monitor and prevent misuse, access, modification or denial of a network accessible resources and computer network. Network security includes the authorization of access to data in a system that is maintained by the network administrator.
The users choose and provided with an ID and password other authentication information that enables them to access programs and information within their authorities. Network security includes a variety of computer networks that are used in daily jobs which may be both public and private that conducts communications and transactions among government agencies, individuals and businesses.
The network can be private like within a company and others that may be open to public access. Network security is used in enterprises, organizations and other institutions. It does explain little as it secures the network as well as overseeing operations and protecting is done. The most simple and common way of protecting a network resource is by assigning it a unique name and unique password.
The network security starts with generally authenticating with a username and a password. As this needs just one detail authenticating username that is the password, it is sometimes termed one-factor authentication. Something the user ‘has’ is also used with the two-factor authentication(for example an ATM card, a security token or dongle or a mobile phone) and with three-factor authentication something the user ‘is’ also used (such as a retinal scan or fingerprint scan).
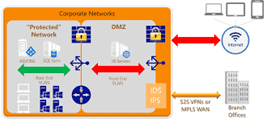
A firewall implements access policies like what services are allowed to be accessed by the network users once it is authenticated. This component might fail to find potentially harmful content like Trojans or computer worms that are being transmitted via the network, to prevent unauthorized access. Antivirus software or an Intrusion Prevention System(IPS) assists in detecting and taking actions against such malware.
The communication between two hosts via a network might be encrypted to maintain privacy. The security management for systems is different for different situations. A small office or home may only need basic security whereas large businesses may need advanced software and hardware and high maintenance to stop malicious attacks from spamming and hacking.