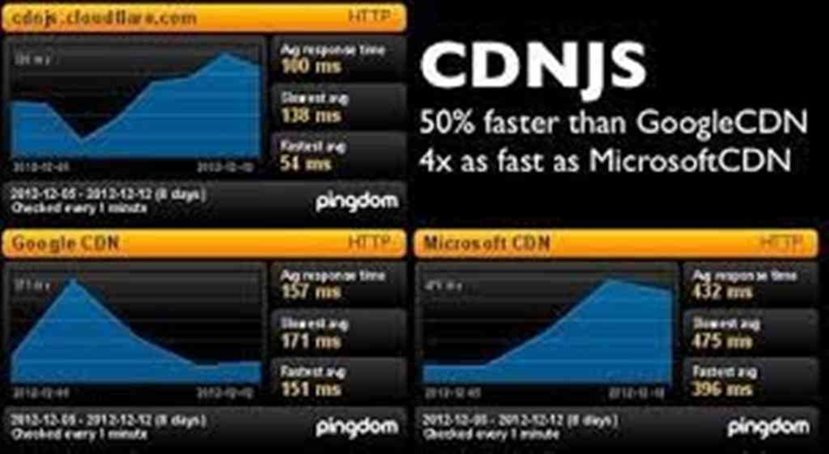
CloudFlare CDNJS Bugs Can Lead to Widespread Supply-chain Attacks
19th July 2021, Kathmandu
Critical bug discovered in Cloudflare CDNJS which could have led to supply-chain attacks. 12.7% of all the websites on the internet use the CDNJS library. Cloudflare has fixed a critical vulnerability in its CDNJs library last month.
The issue could have allowed a threat actor to execute arbitrary commands in the CDNJS library update server which could have resulted in a complete compromise.
RyotaK had discovered the vulnerability and reported it to the company on April 6, 2021. The company stated that no evidence of wild exploitation of this issue.
This bug functions by publishing packages to Cloudflare’s CDNJS using GitHub as well as npm mobilizing it to trigger path transversal attack as well as finally tricking the server into executing arbitrary code finally to achieve RCE
The security researcher had discovered that arbitrary code could be executed after the threat actor performs path traversal from the .tgz file that is published to npm and then overwriting the script which is executed regularly on the server.