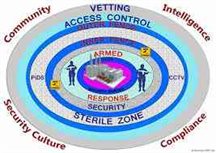
Defense In Depth A Simplistic Model
Defense in Depth: The information must be protected throughout its life span from the initial development of the data to the destruction of that information. No matter what whether at rest or motion the data must be protected. The info might go through different information processing systems, and there are many methods the information systems along with data can be threatened.
Every component of the information processing system must contain its protective methods to protect the information throughout its lifetime adequately. Defense in depth means the building up, layering on the overlapping of security measures. The weakest link is always most significant than the strength of any system. If one protective test fails, there are other several methods to back up and continue the protection in defense in depth strategy.
The three types of controls administrative controls, logical controls, and physical controls can be used to form the basis to build a defense-in-depth strategy. The defense-in-depth can be understood as three distinct planes or layers laid one on top of the other using this approach.
The further knowledge about defense-in-depth can be earned by thinking of it as forming the layers of an onion with data at the core of the onion, people the next outer layer of the onion, and network security, application security and host-based security forming the outermost shells of the onion. The two approaches are valid equally, and both provide an essential knowledge about the implementation of a decent defense-in-depth strategy