How to Check if Your iPhone is Hacked?
23rd March 2023, Kathmandu
iPhones have become an essential aspect of our daily lives. We use them for important activities like shopping online and storing private data. With features like Apple Pay, people can easily connect their debit or credit card to their iOS gadgets.
These mobile devices have become so vital that the thought of someone else having access to them (especially without our knowledge or permission) is disturbing.
Not to worry, this piece will help erase suspicions of your phone being hacked. We will give you actionable tips to detect if your iPhone has been hacked. Aside from helping you ascertain if someone else has access to your phone, we will also help you with measures you can use to protect yourself better.
Signs that Your iPhone May Be Hacked
Before examining how to check if someone else has access to your iPhone, let’s examine possible signs that this is the case. Below are some clues that a third party has access to your gadget:
- unauthorized apps are installed on your phone
- internet subscription you don’t recognize
- battery draining faster than usual
Unauthorized Apps Are Installed on Your Phone
Having applications you do not remember installing on your iPhone signifies your device may be hacked. If they are not developer software programs already installed on your phone pre-purchase, they are most likely malicious. Regardless of their source, they can be used for jailbreaking and prevent you from updating your operating system’s version. It also gives cyber-terrorists backdoor access to sensitive information. This approach is tricky because the hacker may even hide the program from appearing in your menu.
Internet Subscription and Battery Draining Faster than Usual
This is another very evident sign that “you are not the only one” using your device. How you use your gadget determines how fast the battery power will run out. This principle also applies to your internet subscription bundle. Data transfer causes both items to drain very fast. Although iPhone batteries wear out with time, data bundles do not suffer the same fate. So you should be concerned if your battery and data bundles run out even when your phone is idle.
There are several other signs that someone else has access to your iOS mobile device. They include background noise, lagging performance, strange text messages, interference during calls, or suspicious or seemingly self-executing actions from your iPhone.
How to Check if Your iPhone is Hacked
You probably noticed one or more of the abovementioned signs. However, you want proof that your iPhone has been hacked. Here are ways to confirm whether your device is safe properly:
- Use codes to check for specific functions
- Run an antivirus scan
Use Codes to Check Specific Functions
There are various codes to ascertain if certain functions have been compromised. For example, you can use the *#21# to check if your phone is tracked. This mobile hack code also helps you confirm if anyone is diverting your private information and the number to which they redirect it. If you notice any issues, use ##002# to revoke the forwarding of all calls and data.
Run an Antivirus Scan
While codes are efficient and easy to use, they are limited and may not detect certain security loopholes. This is why you need an antivirus software program. Install it on your iPhone and run a scan to check for irregularities. This approach can help you identify malware or suspicious applications that are backdoors for data theft. Some special cybersecurity packages include Clario, Norton, TotalAV, McAfee, etc.
How to Protect Your Device
Ensuring your device is safe is vital, whether your iPhone has been hacked. The steps below can help you prevent a security breach or overcome one:
- Update your iPhone Operating System
- Delete suspicious applications
- Use multifactor authentication methods
- Avoid suspicious links
Update Your iPhone Operating System
Besides optimizing gadget performance, Apple launches OS updates to introduce security patches. Dedicated experts working with the phone manufacturing company understand the latest safety threats and employ measures to mitigate them. You should constantly update your phone with the recent compatible operating system upgrade.
Follow these steps to update your device:
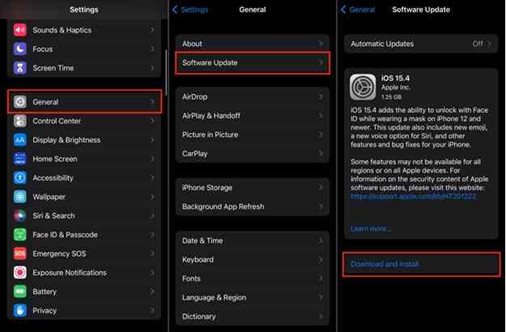 Delete Suspicious Applications
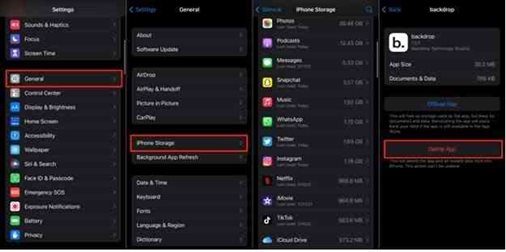
Delete Suspicious Applications
Go through your phone, identify applications you do not remember installing, and delete them. Follow the steps below to remove an app from your phone settings menu:
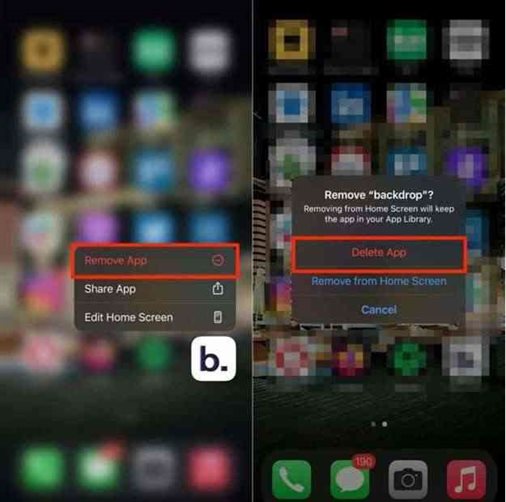
 Alternatively, you can remove apps from your Home Screen:
Alternatively, you can remove apps from your Home Screen:
 Use Multi-Factor Authentication Methods
Use Multi-Factor Authentication Methods
You can prevent possible security exploits by upgrading the measures used in accessing your account. Introduce the Two-Factor Authentication method to your iCloud account and similar services. This makes it difficult for cyber-terrorists to bypass your security – even when they have your passwords.
Avoid Suspicious Links
While improving your access measures is effective, it will not work well if you continuously expose your device to security threats. Avoid clicking on suspicious links, especially those promising freebies and gifts that are too good to be true.
Conclusion
Apple operates a closed ecosystem, so there are reduced chances of cybersecurity threats. However, an intent hacker still needs to bypass safety measures and access data on your phone. Nonetheless, you can use the measures listed in this guide to protect yourself adequately.







