Spies Can Now Listen to Conversations by Watching a Light Bulb in a Room
21st June 2020, Kathmandu
It may be difficult to believe but the light is watching you and in this case, quite literally. With something known as the Lamphone attack, spies can listen to your conversation watching a light bulb in your room.
Yes, it is based on the hypothesis that you are in a room with a light bulb hanging in there. And, it should be visible from a window.
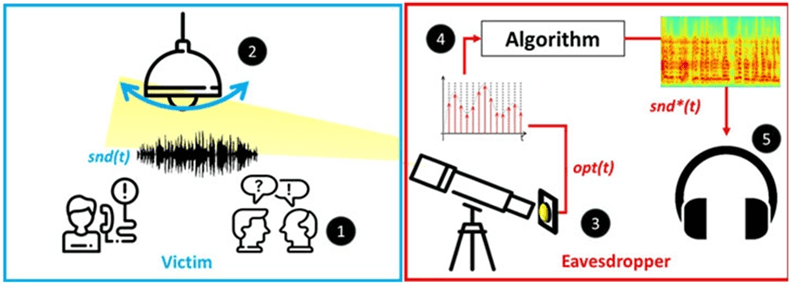
A team of cybersecurity researchers has found out a novel side-channel attacking technique being used to eavesdrop on conversations. This attack recovers full sound from a conversation by measuring the amount of light the bulb emits.
The credit of the findings of this technique called “Lamphone” goes to researchers at Ben-Gurion University of the Negev and the Weizmann Institute of Science.
How does Lamphone Attack Exploit Light Bulbs?
Basically, eavesdroppers capture sound waves optically through an electro-optical sensor directed at the light bulb. These minuscule sound waves are used to recover speech and also recognize music.
So, the main premise of this attack is to detect vibrations from the hanging bulbs as a result of air pressure fluctuations. This phenomenon occurs naturally when the sound waves hit the bulb surfaces which we can’t normally observe.
By measuring the tiniest changes in the bulb’s output due to the vibration in its surface, threat actors can recover snippets of conversations.
God is in the details!
Except for this time, it’s a privacy threat that is.
You May Also Like: Cyber-attacks Related to Video Games on the Rise
The Theory Behind this Novel Side-channel Attack
The assumptions are based upon the presence of a victim inside a room or office that contains a hanging light bulb.
According to the researcher, the eavesdropper is a malicious entity that is interested in spying on the victim. By retrieving the victim’s conversation, the malicious entity can misuse the information provided in the conversation.
Threats to the victim include identity theft, extortion, and so on.
So, what are the tools that can achieve the Lamphone attack?
Firstly, an attacker would need a telescope to focus on the target which is the hanging bulb.
Another thing is an electro-optical sensor mounted to the telescope. This sensor’s job is to transform the captured photons from the light source (bulb) into electric current.
Also, an analog-to-digital converter to convert the sensor output to a digital signal.
Finally, they would need a sound recovery software that converts the input optical signals into audio signals.
Lamphone Attack Demonstration
The researchers managed to recover an audible extract of POTUS Donald Trump’s speech. Furthermore, they reproduced a recording of Coldplay’s “Clocks” and the Beatles’ “Let It Be”.
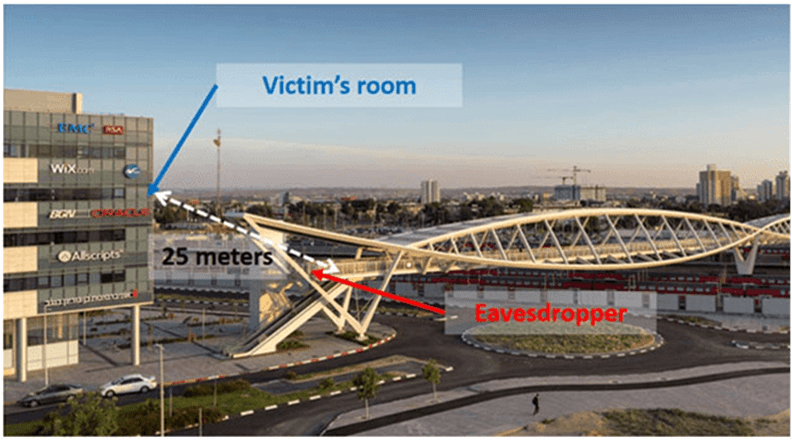
On top of that, the attacker doesn’t have to be within the close vicinity of the victim. In fact, this approach enables the initiation of the eavesdropping at least 25 meters away from the target. Thanks to the telescope.
What’s more concerning is that attackers don’t require a malware that attacks the victim’s device. It’s an entirely external scenario.
Preventing the Attack
The research clearly mentions that the attack is more possible in a real-time scenario. Moreover, the efficiency of the attack is based on spying from a long distance.
However, some limitations of this attack can help implement effective countermeasures.
As mentioned earlier, this attack only works if the target light bulb is in sight. So, covering the bulb with a decorative cover should do the trick.
Likewise, dimming the amount of light emitted from the bulb can also counter the attack.
Secondly, since detecting vibrations of the bulb has a vital part in this attack, it can’t detect lower volumes. This means that the conversation or sound in the rooms should be loud enough to generate vibrations.
If you have a bulb with thick glasses or the one that controls light emission capability, you are immune to this attack.
What are your thoughts on this?
Please share your thoughts in the comments.
Also Read: Ways To Prevent Cyber Attacks – Nepal Vulnerable To Cyber Attacks