Microsoft Warned about an Alert Over Sneaky Phishing Attack
3rd August 2021, Kathmandu
Microsoft has issued an alert about a crafty phishing attack.
Microsoft’s Security Intelligence team has issued an alert to Office 365 users and administrators to watch out for a sneaky phishing email with fake sender addresses.
This alert was put out after careful observation over an active campaign targeting Office 365 companies with cogent emails and various strategies to detour phishing detection, including an Office 365 phishing page, a jeoparded SharePoint sites, and Google cloud web that Microsoft put out an alert after observing an active campaign targeting Office 365 organizations with convincing emails and various strategies to detour phishing detection, including an Office 365 phishing page, Google cloud web app hosting, and a compromised SharePoint site that is longing hosts to write in their credentials.
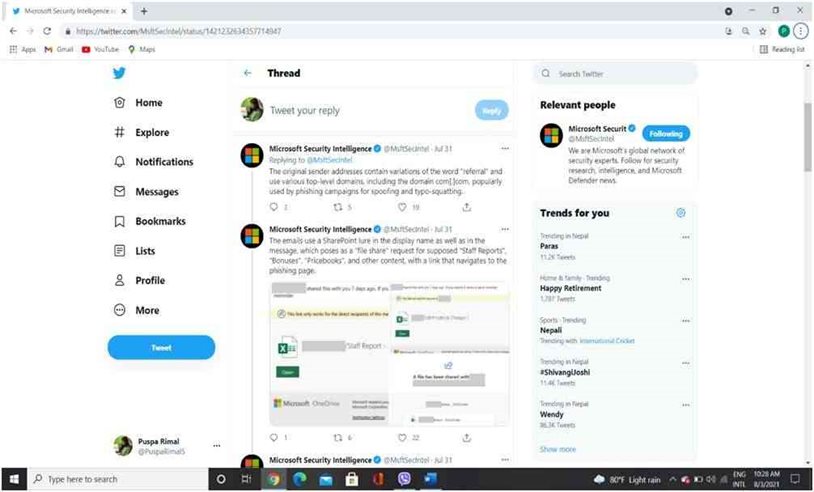
In a streamlined Microsoft, counterintelligence said, “An active phishing campaign is employing a crafty combination of legitimate-looking original sender email addresses, spoofed display sender addresses that contain the target usernames and domains, and display names that mimic legitimate services to undertake and slip through email filters.”
“The disparities of the word “referral” is hold by the actual sender addresses and utilize several top-level domains, which includes the domain com[.]com, popularly employed by phishing campaigns for spoofing and typo-squatting.”
Phishing continues to be a difficult problem for businesses to kill, requiring regularly updated phishing awareness training and technical solutions, like multi-factor authentication on all accounts – which both Microsoft and CISA highly recommend.
Phishing might have been the main component of business email compromise attacks, which sum Americans quite $4.2 billion last year, accordant with the FBI’s latest figures. It’s much costlier than illustrious ransomware attacks. BEC, which depends on compromised email accounts or email addresses that are almost similar to legal ones, its hard to filter as they mix within normal, expected traffic.
Microsoft SharePoint has been used in the display name to tempt victims to click the link by the phishing group. The email poses as a “file share” request to enter bogus “Bonuses,” “Staff Reports,” “Pricebooks,” and other content hosted during an assumed Excel spreadsheet. It also has a link that traverses to the phishing page and many of Microsoft branding.
While convincing Microsoft logos are littered across the e-mail, the most phishing URL relies on a Google storage resource that points the victim to the Google App Engine domain AppSpot – a place to host web applications.
“Two URLs having deformed HTTP headers are contained in the emails. The main phishing URL is thought be a Google storage resource that clicks to an AppSpot domain that urges the user to check in before finally serving another Google User Complacent realm along with an Office 365 phishing page.” said Microsoft.
The second URL has been integrated within the message settings links the host to a compromised SharePoint site. Both URLs mandate sign-in to urge to the ultimate page, permitting the attack to bypass sandboxes.
According to Microsoft, this crusade is “sneakier than usual.”
Microsoft has been hyping its ‘Safe Links’ Defender for Office 365 phishing protection function that ‘detonates’ phishing email at the motive a user taps on a link that equals its list of known phishing pages.
There has been a publication of details about the architectures connected to the spoofed emails mimicking SharePoint and other services on GitHub by Microsoft for credential phishing.
“The operator is additionally known to utilize legal URL infrastructure like Google, Microsoft, Digital Ocean and Google to host their phishing pages,” Microsoft added.