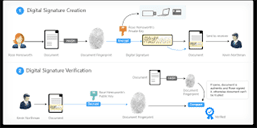
What exactly is a digital signature?
Just as a handwritten signature is affixed to a printed letter for verification that the letter originated from its purported sender, digital signature performs the same task for an electronic message.
A digital signature is an encrypted version of a message digest, attached together with a message. A secure digital signature system consists of two parts: A method of signing a document such that forgery is detected, and A method of verifying that a signature was actually generated by whomever it represents Asymmetric/ Public key vs. Symmetric/ Secret key: which cryptography system is better? A combination of both. The action of encrypting information with public-key cryptography is significantly slower than encrypting with a secret key. However the drawback of the secret-key system is that, secret keys must be transmitted either manually or through a communication channel, and there may be a chance that others can discover the secret keys during transmission.
This is not a problem with public-key cryptography, as private keys never need to be transmitted or revealed to anyone. Each user has sole responsibility for protecting his or her private key. So, in practice public-key cryptography is used with secret-key cryptography to get the best of both worlds. A system that uses public-key cryptography first generates a secret key and uses the secret key to encrypt the message. Public-key cryptography key is then used to encrypt the secret key, which then is attached to the secret key-encrypted message.