Why Is The Cybersecurity Of Nepalese Banks So Weak?
The hacking case that occurred on 18th October 2017 (1st Kartik 2074) has been revealed to be the carelessness of the staff and management of NIC Asia Bank. The report published by the bank itself suggests that the cybersecurity of the bank is too weak and handled carelessly.
The bank in co-operation with Rastrya Bank ordered an Indian company named KMPG to study and prepare a report accordingly about the flaws of the system by bypassing the Nepal Police’s Central Investigation Bureau(CIB).
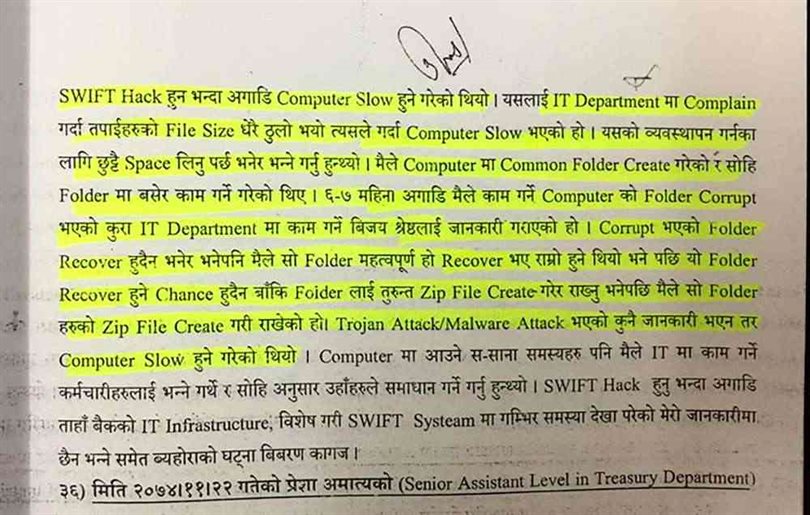
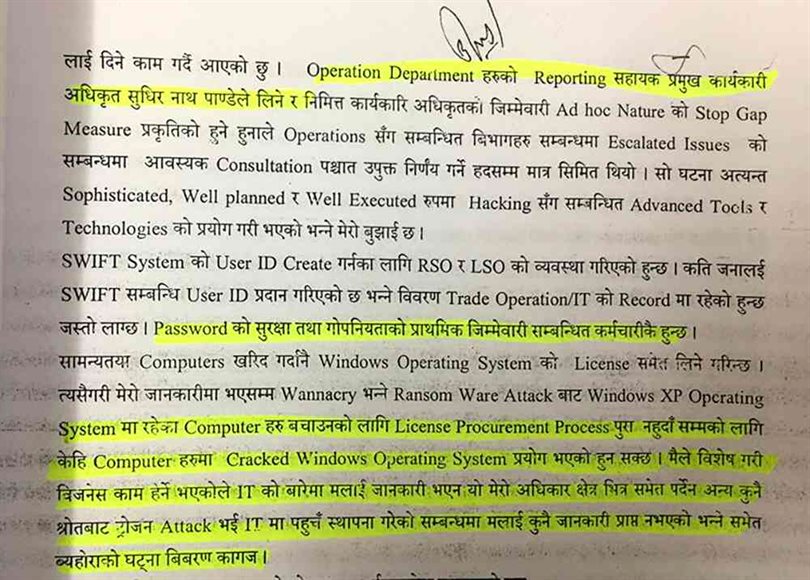
The report submitted by KMPG through Rastrya Bank to the CIB has concealed the fault of the staff and management of NIC Asia Bank. However, the bank’s cybersecurity has been proven to be inadequate.
During the investigation, the higher ranked staff members and management weren’t under the police radar, the Indian company only talked about the technical issues with the bank staff, one of the employees said, “The fact that the bank that safely keeps the money of citizens is careless can be seen clearly on the report provided by KMPG.”

The same report points out that a legal case has been filed at Patan high court against 13 account holders from foreign banks located at eight countries. A 69 paged prosecution provided by the court to Nepal Live claims that not just the management heads but also the IT department of the bank think cyber security isn’t reliable and responsive.
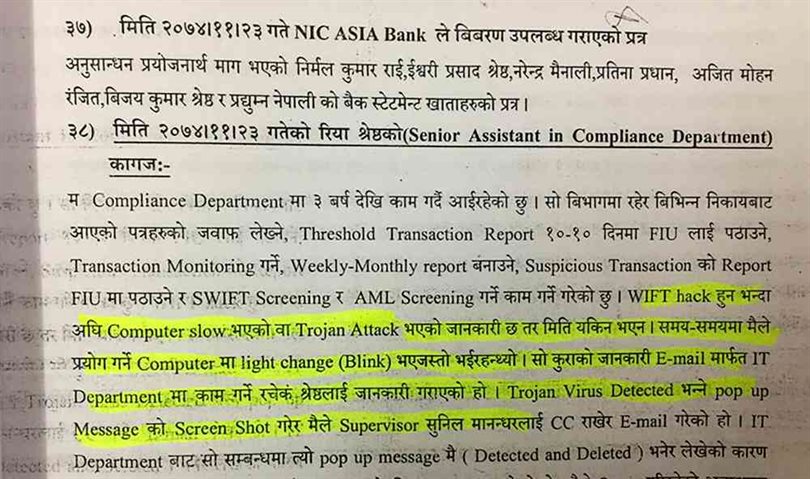
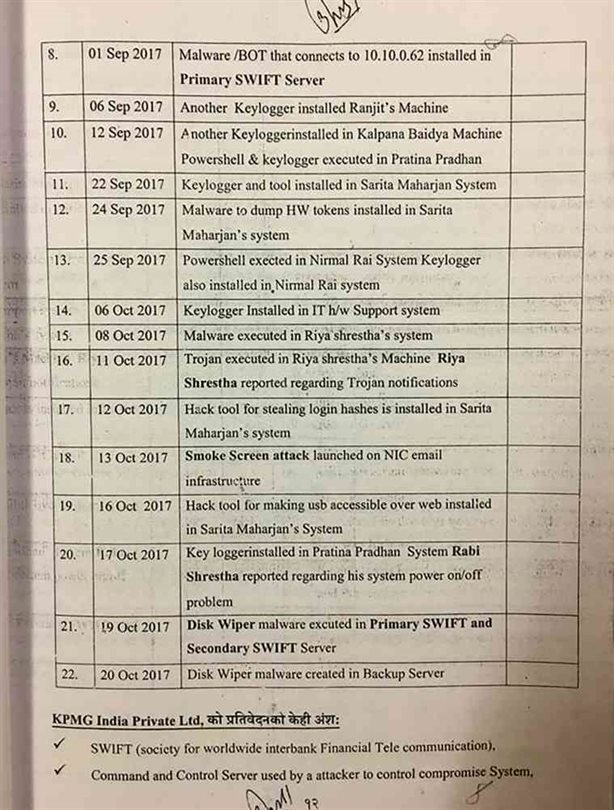
The 11th and 12th pages of the prosecution include the ‘Hack Timeline’ prepared by KMPG, India. It mentions that the wrong information delivered by the cyber combination of the bank along with the frequent cyber attacks that occurred. In addition to these, the timeline includes the use of ‘Keylogger’ software by one of the users along with numerous ‘Malware’ to ‘Smokescreen’ attacks.
The timeline also says that the emails used by the bank were attacked a few days before the bank hack. Usernames and passwords of Mohan Ranjit, Pradhumna Nepali and Patina Pradhan were used to transfer 46 Crore 56 Lakh 50 thousand 5 hundred 5 rupees via swift message. The employees that were mentioned in the prosecution letter stated that they reported the various issues with the cyber system to the concerned authority.
Employees working in the IT department said that they weren’t well trained about swift technology which suggests the carelessness of the bank. The late response is shown by the bank to check the security issues even after knowing that the attacks occurred on 1st of Kartik add up to the negligence shown by the authorities.
The CEO during the hack, and present Deputy CEO, Sudhir Kumar Pandey stated, “No fixed scheduled swift training is conducted for the staff members.” He added Nepal lacks the organizations to provide swift training. His statement mentions, “Training in Nepal are conducted rarely by International companies.”
Roshan Kumar Neupane, recently appointed as the CEO stated, “Sudhir Kumar Pandey takes operational department’s reports”. He added that the swift password and its privacy is the priority of the staff themselves. He says that generally computers are bought with the Windows OS installed. However, cracked OS are also installed sometimes.
Cracked OS being used in computers of banks where electronic payment is carried out is a simple invitation for hackers to hack the system.
Deputy Governor of Rastrya Bank, Chintamadi Sapkota says, “Cracked windows should not be used at banks. The bank is a highly sensitive organization, so using pirated software can prove to be dangerous. There are IT guidelines for the banks to follow, but most banks don’t seem to follow it.”
The hacking case of NIC Asia bank isn’t being investigated the way it should have been. The conclusion of prosecution letter provided by the court raises a question on the sincerity of the employees. This incident portrays the lack of proper cybersecurity in many banks of Nepal.






