Wild Pressure APT Returns with New Malware Targeting Windows and macOS
9th July 2021, Kathmandu
WildPressure, an advanced persistent threat (APT) actor active within the Middle East since August 2019, has added a replacement malware variant that targets both Windows and macOS devices.
A malicious campaign that has focused on Middle Eastern industry-related entities since 2019 has resurfaced with an upgraded malware toolset that attacks both Windows and macOS operating systems. This symbolizes the expansion of both targeting and threat distribution strategies.
Russian cybersecurity companies attribute it to the Advanced Persistent Threat (APT) that tracks attacks. WildPressure, “Victims are believed to be within the oil and gas industry.
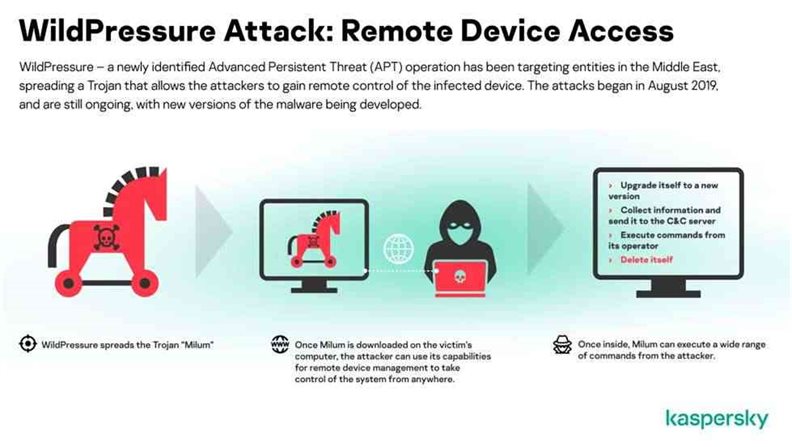
WildPressure was first revealed in March 2020 supported a malware operation that distributes a full-featured C ++ Trojan called “Milum” that permits threat attackers to remotely control a compromised device. The attack is claimed to possess started as early as August 2019.
The malware uses the JSON format for configuration data and as a C2 communication protocol over HTTP also. Inside the encrypted communications within the HTTP POST requests, Kaspersky found several interesting fields. One among them shows the malware version – 1.0.1. A version number like this means an early stage of development. Other fields suggest the existence of, at the very least, plans for non – C++ versions.
 “We used rented OVH and Netzbetrieb virtual private servers (VPS) and domains registered with the Domains by Proxy anonymization service for our campaign infrastructure,” said Kaspersky researcher Denis Legezo last year
“We used rented OVH and Netzbetrieb virtual private servers (VPS) and domains registered with the Domains by Proxy anonymization service for our campaign infrastructure,” said Kaspersky researcher Denis Legezo last year
Since then, new malware samples are unearthed to be used within the Wild Pressure campaign. This includes a replacement version of C ++ Milum Trojan, a corresponding VBScript variant with an equivalent version number, and a Python script named “Guard” that works on both Windows and macOS.
“We were ready to sinkhole one among the WildPressure C2 domains (upiserversys1212[.]com) in September 2019. The overwhelming majority of visitor IPs were also from the center East, and that we believe the remainder were network scanners, TOR exit nodes, or VPN connections,” the researchers said.
Now the group resurfaced with the upgraded malware targeting both Windows and macOS systems. This variant “was delivered during a package, including the malware, Python library, and a script named ‘Guard’. This enabled the malware to launch both on Windows and macOS with little additional effort. Once infecting the device, the malware runs operating system-dependent code for persistence and data gathering. On Windows, the script is bundled into an executable with a PyInstaller. The Python trojan is additionally capable of checking whether security solutions are being run on a tool,” the researchers said.
The malware supports multiple commands, including the power to download and upload arbitrary files, execute commands, update itself, and pack up, remove persistence, and therefore the script file from the infected host.
 “To date, we don’t have any data regarding Milum’s spreading mechanism. A campaign that’s, apparently, exclusively targeting entities within the Middle East (at least a number of them are industrial-related) are some things that automatically attract the eye of any analyst. Any similarities should be considered weak in terms of attribution, and should simply be techniques copied from previous well-known cases. Indeed, this “learning from experienced attackers” cycle has been adopted by some interesting new actors in recent years,” Kaspersky noted.
“To date, we don’t have any data regarding Milum’s spreading mechanism. A campaign that’s, apparently, exclusively targeting entities within the Middle East (at least a number of them are industrial-related) are some things that automatically attract the eye of any analyst. Any similarities should be considered weak in terms of attribution, and should simply be techniques copied from previous well-known cases. Indeed, this “learning from experienced attackers” cycle has been adopted by some interesting new actors in recent years,” Kaspersky noted.
Why was it called Milum?
All the aforementioned C++ Trojans are compiled as standalone PE files, originally named Milum46_Win32.exe. The word ‘milum’ is employed within the C++ class names inside the malware, so Kaspersky named the Trojan after it.
Another distinctive characteristic is that the malware exports many Zlib compression functions, like zlibVersion(), inflate(), or deflate(). This compression is required for C2 communication, but actually, there’s no got to export them within the case of a standalone application.
The JSON configuration fields aren’t limited to only the version and programming language; the campaign operators also use target IDs that are found within the samples. Among them, Kaspersky found HatLandM30 and HatLandid3 – neither of which we are conversant in.