IT Audit in Accordance with COBIT Standard, Suman Thapaliya
4th June 2021, Kathmandu
IT audit is the process of gathering and evaluating evidence-based on which one can evaluate the performance of IT systems, i.e., to determine whether the operation of information systems in the function of preserving the property and maintain data integrity. It is also necessary to determine whether IS enables the effective achievement of business objectives and whether system resources are effective and efficient. These must be understood to consider how they can be used together, COBIT with acting as the consolidator.
COBIT
COBIT is the worldwide accepted standard that prescribes areas and individual controls for IT governance, informatics, and related IT processes. COBIT combines business and IT goals, providing the ability to monitor the maturity of the information metric system. The practice recommended by COBIT is the mixture of knowledge of numerous experts as a result of good practice, applicable in any organization.
Overall, COBIT ensures the quality, control, and reliability of information systems in an organization, which is also the most important aspect of every modern business.
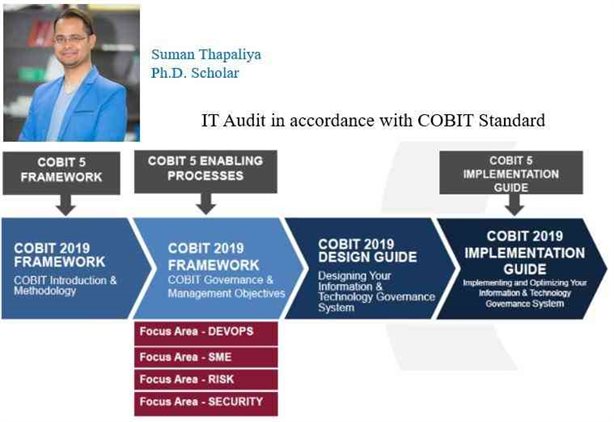
The first version of COBIT was created as a tool to support the performance of an audit of financial statements. Still, it continues further to develop following the development of the IT role in business. Figure 2 shows the development of the COBIT framework and the roles it has had through its development and upgrading. COBIT consists of 34 key business control processes describing each process model of maturity.
COBIT FRAMEWORK
COBIT has a high position in business frameworks and has been recognized under various international standards, including ITIL, CMMI, COSO, PRINCE2, TOGAF, PMBOK, TOGAF, and ISO 27000.
The latest COBIT version 5 came out in April 2012 and consolidated the principles of COBIT 4.1, Risk IT Frameworks, and Val IT 2.0.
Various COBIT Components are:
- Framework
- Process Description
- Control Objectives
- Maturity Models
- Management Guidelines

 Critics maintained that COBIT 5.0 encouraged paperwork and rote rules rather than merely promoting IT governance engagements and improving accountability. However, COBIT 5.0 addressed all the criticisms sustainably.
Critics maintained that COBIT 5.0 encouraged paperwork and rote rules rather than merely promoting IT governance engagements and improving accountability. However, COBIT 5.0 addressed all the criticisms sustainably.
In several cases, COBIT 5.0 has been appreciated for reducing the risk of IT implementations.
From the point of control and information systems, audit COBIT determines 18 applications and 6 process controls. Assessment of maturity of IT governance processes is in the range of 0 to 5.
0. There are no processes, the process of IT governance does not exist.
- In initial processes, management is not aware of the importance of IT governance. However, there are no formal procedures, management, and oversight of information technology based on individual and uncontrolled based, and actions are taken on a case by case basis.
2. There are no standards, nor corporate rules, nor obligations and responsibilities regarding this issue.
3. Defined processes, IT governance procedures are prescribed and documented and constantly improved through formal training and education. Although they formally exist, procedures and corporate rules are not sophisticated, mature, nor customized to organization business. They only represent the formalization of existing procedures. Although procedures exist, the responsibility for its execution is on the individuals. Keeping in mind that there is no system supervision, it is unlikely that one can detect anomalies regarding this matter.
4. Very sophisticated IT governance objectives closely aligned with the business objectives are being set.
5. Optimized processes, IT governance processes are brought to the optimal level, and the company is a leader in the area. Complete transparency in IT governance governs, corporate bodies have actual supervision over information technology through a series of formal mechanisms.
To satisfy business objectives, information needs to conform to certain control criteria, which COBIT refers to as business requirements for information.
- Effectiveness deals with information being relevant and pertinent to the business process and being delivered in a timely, correct, consistent and usable manner.
- Efficiency concerns the provision of information through the optimal use of resources.
- Confidentiality concerns the protection of sensitive information from unauthorized disclosure.
· Integrity relates to the accuracy and completeness of the information and its validity by business values and expectations. - Availability relates to information being available when required by the business process now and in the future.
- Reliability relates to the provision of appropriate information for management to operate the entity and exercise its fiduciary and governance responsibilities.
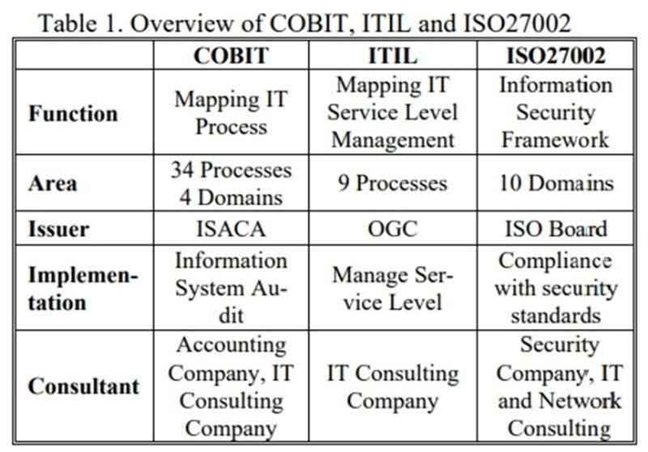
- ITIL and ISO 27002, 27001 Standards
ITIL is based on defining best practice processes for IT service management and support rather than defining a broad-based control framework. IT service management is concerned with planning, sourcing, designing, implementing, operating, supporting, and improving IT services appropriate to business needs. ITIL provides a comprehensive, consistent and coherent best practice framework for IT service management and related processes, promoting a high-quality approach for achieving business effectiveness and efficiency in IT service management. ITIL is intended to underpin but not dictate the business processes of an organization.
The role of the ITIL framework is to describe approaches, functions, roles, and processes upon which organizations may base their own practices and give guidance at the lowest level that is generally applicable. Below that level, and to implement ITIL in an organization, specific knowledge of its business processes must drive ITIL for optimum effectiveness. V3, the most significant development has been the move from a process-based framework to a more comprehensive structure reflecting the life cycle of IT services.
Its goal is to provide information to parties responsible for implementing information security within an organization. It can be seen as a best practice for developing and maintaining security standards and management practices within an organization to improve reliability on information security in inter-organizational relationships. It defines 133 security control strategies under 11 major headings. The standard emphasizes the importance of risk management and clarifies that it is not necessary to implement every stated guideline, only those that are relevant.
Overview of COBIT, ITIL, and ISO 27002 Standards
 Benefit of COBIT
Benefit of COBIT
This raises the success rate of businesses and raises other challenging and complex management and governance concerns for the security professionals, enterprise leaders, and governance specialists. COBIT 5.0 is the exact solution modern businesses are asking for.
Conclusion
IT processes while ITIL aims to map IT service level management and ISO27002 provides guidelines for implementing a standardized information security framework. COBIT consists of 4 domains and 34 processes required to implement the information system audit.
From 1 June to 31 July 2009, It provides a comparison of companies in respect of major areas of information security and IT governance. COBIT is increasingly popular for planning IT audit activity and is adopted by 69 percent of respondents. These frameworks deliver a structured approach to planning and focus the IT audit on the business and technological risks of the organization. COBIT, ITIL, ISO 17799, and ISO 27001 are the group of most commonly used methodologies by companies regarding IT security and IT governance.
Internal Audit should have a direct line to executive management and the Audit Committee. By cascading top-level opinions on the value and content of Internal Audit’s outputs and communicating information on the business issues, the function can heighten its visibility. To maintain that position, it needs to develop a closer relationship with the business while maintaining its independence and objectivity. This powerful combination of technical and business know-how, underpinned by an understanding of operational and technology risk, can turn the function from a cost center to a value builder.
While the modern world is gearing towards several emerging technologies, including consumerization, cloud computing, social media, big data, and mobility, information and IT are easily the new currency. As a result, new businesses demand that risk scenarios are better met with the power of information.
Suman Thapaliya
Ph.D. Scholar (Lincoln University, College)