29th August 2021, Kathmandu
Microsoft is an admonishment of a widespread credential phishing campaign that leverages open redirector links in email communications as a vector to illude users into visiting malevolent websites while efficaciously bypassing security software.
“Assailants amalgamate these links with gregarious engineering baits that impersonate well-kenned productivity implements and accommodations to lure users into clicking,” Microsoft 365 Advocator Threat Perspicacity Team verbally expressed in a report published this week.
“Doing so leads to a series of redirections including a CAPTCHA verification page that integrates a sense of legitimacy and endeavors to eschew some automated analysis systems afore taking the utilizer to a fictitiously unauthentic sign-in page. This ultimately leads to credential compromise, which opens the utilizer and their organization to other attacks.”
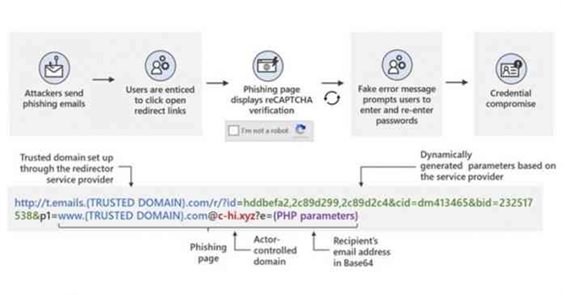
Albeit redirect links in email messages accommodate a vital implement to take recipients to third-party websites or track click rates and quantify the prosperity of sales and marketing campaigns, the same technique can be abused by adversaries to redirect such links to their own infrastructure, at the same time keeping the trusted domain in the full URL intact to eschew analysis by anti-malware engines, even when users endeavor to hover on links to check for any designations of suspicious content.
In order to lead potential victims to phishing sites, the redirect URLs embedded in the message are set up utilizing a legitimate accommodation, while the final actor-controlled domains contained in the link leverage top-level domains .xyz, .club, .shop, and .online (e.g. “c-tl[.]xyz”), but which are passed as parameters so as to sneak past email gateway solutions.
Microsoft verbalized it optically canvassed at least 350 unique phishing domains as a component of the campaign another endeavor to obscure detection underscoring the campaign’s efficacious utilization of convincing gregarious engineering lures that purport to be notification messages from apps like Office 365 and Zoom, a well-crafted detection evasion technique, and a durable infrastructure to carry out the assailants.
Clicking the specially-crafted links redirects the users -> clicking the specially-crafted link redirects the users
“This not only shows the scale with which this assailment is being conducted, but it withal demonstrates how much the assailers are investing in it, denoting potentially paramount payoffs,” the researcher verbalized.
To give the assailment a veneer of authenticity, clicking the specially-crafted links redirects the users to a maleficent landing page that employs Google reCAPTCHA to block any dynamic scanning endeavors. Upon completion of the CAPTCHA verification, the victims are exhibited a fraudulent authenticate page mimicking a kenned accommodation like Microsoft Office 365, only to swipe their passwords upon submitting the information.
“This phishing campaign exemplifies the impeccable storm of [social engineering, detection evasion, and an astronomically immense assailment infrastructure] in its endeavor to purloin credentials and ultimately infiltrate a network,” the researchers noted. “And given that 91% of all cyberattacks originate with email, organizations must consequently have a security solution that will provide them a multi-layered bulwark against these types of attacks.”