OWASP Top 10 Web Security Vulnerabilities
22nd October 2021, Kathmandu
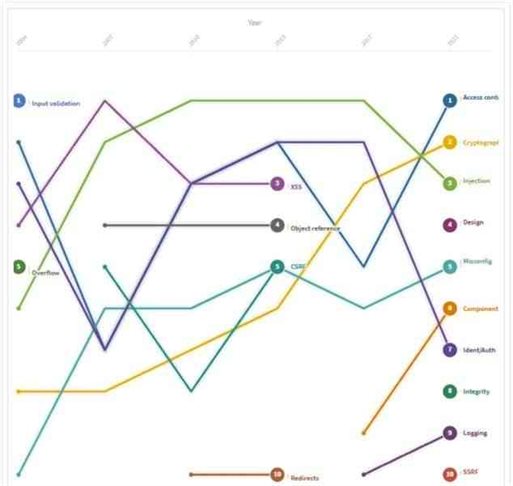
The line graph above presents the OWASP Top 10 Security Vulnerabilities from the year 2004 to 2021.
The OWASP Top 10 Security Risks and Vulnerabilities report aids business companies and web applications to identify vulnerabilities that are frequently exploited by attackers and provides recommendations for preventing these attacks.
In the year 2004, input validation was the most critical security vulnerability followed by broken access control and broken authentication.
Input validation vulnerability occurs when data and information from web requests are not validated prior to being used by a web application.
Broken access control is a security vulnerability where authorized users and restrictions on what those users are allowed to do are not properly defined.
A broken authentication vulnerability is when the necessary credentials and session tokens of users are not secured properly.
Cross-Site Scripting (XSS), Buffer Overflow, Injection, and Cryptographic failures are other web and security vulnerabilities that were included in the OWASP Top 10 list in 2004. Cross-site scripting, injection flaws, and insecure direct object reference were the top three most critical security vulnerabilities of the year 2007.
XSS is a security vulnerability that occurs when an application system delivers user-supplied data to a web browser without verifying or encoding the data beforehand.
Injection flaws are another common web application vulnerability where the user input data are communicated to an interpreter as a part of a query or command.
When a developer reveals a reference to an internal implementation object like file, database records, or directories, in the form of a URL or form parameter, it is known as an insecure direct object reference.
Hackers can potentially gain unauthorized access to other objects by manipulating those references.
CSRF, misconfiguration, broken access control, broken authentication, and cryptographic failures are other security vulnerabilities that fall under OWASP Top 10 list of 2007.
In both the years 2010 and 2013, injection flaws were the most common security vulnerability along with broken access control, broken authentication, XSS, and insecure direct object reference.
The other web application and security vulnerabilities that were included in the OWASP Top 10 of 2010 and 2013 were security misconfiguration, cryptographic failures, CSRF, and unvalidated redirects respectively.
Injection flaws were again the most critical and common security vulnerability of the year 2017 followed by broken authentication and cryptographic failures.
Broken access controls, security misconfigurations, using components with a known vulnerability, and insufficient logging were other common web application vulnerabilities that made to the OWASP Top 10 Security Vulnerabilities of 2017.
According to the OWASP Top 10 Security Vulnerabilities of the year 2021, broken access control is the top and most common security vulnerability followed by cryptographic failures and injection flaws respectively.
Cryptographic failures, previously known as sensitive data exposure, are a vulnerability related to the failure of cryptographic algorithms that could potentially lead to unwanted exposure of sensitive information.
Along with these, insecure design and security misconfiguration take fourth and fifth place in the list.
Insecure design mainly focuses on risks and threats regarding design flaws. Security misconfiguration includes wrongly configuring permissions on cloud services, installing or enabling unnecessary features, and so on.
Using components with known vulnerability, broken authentication, software, and data integrity failures, insufficient logging and server-side request forgery (SSRF) takes sixth, seventh, eighth, ninth, and tenth position respectively in the OWASP Top 10 Security Vulnerabilities of 2021.