CERT-In Warned Users Against Instagram Phishing Attacks
30th October 2020, Kathmandu
Social media can be a fun way to interact with your friends and families, but it could come with its own set of cons, one being Phishing attacks. Phishing attacks and information theft in social media aren’t new, but it is getting dangerous with time.
Scammers have been using the favorite photo-sharing app, Instagram, as a popular medium to steal data and personal information. But don’t worry; they can’t steal your data right away without you doing anything.
Phishing Attack on Instagram
The Indian Computer Emergency Response Team (CERT-In), under the Ministry of Electronics & Information Technology, Government of India, has warned users about the phishing attacks via its Twitter post.
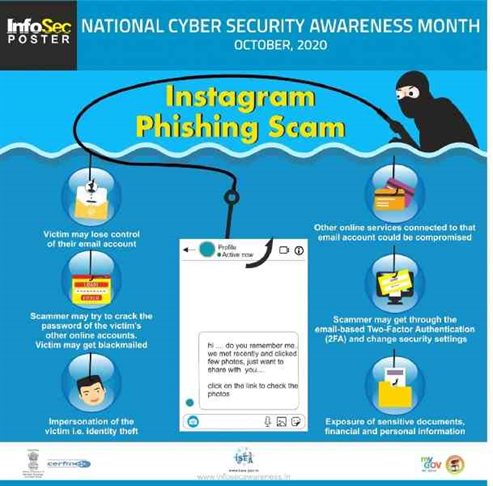
Cert-In has included a photo explaining the Phishing Attacks on Instagram DMs and the consequences you have to bear if scammers steal your information. The message in the DMs may be related to anything. Still, generally, scammers will attach a link will be which they will ask you to click.
With a click at this link, users might lose their email address. Even other online services connected to the email account might be compromised, warns the Twitter post.
With full control of the email address, scammers might try to crack other online accounts’ passwords, further blackmailing the victim. Or even the scammer may impersonate as the victim in their social media handles.
Scammers and frauds with the email address could quickly get through the two-factor authentication (2FA). Then they could even change the security settings of email and other associated accounts. After that, scammers get to hold onto sensitive documents, financial and personal information.
Globally, October is being celebrated as National Cyber Security Awareness Month(NCASM). And the CERT-In is sharing cybersecurity tips and awareness posts throughout October via its Twitter handle.
CERT-In had shared the post about Phishing Attacks on Instagram through the caption: “NATIONAL CYBERSECURITY AWARENESS MONTH (NCSAM).”
⦁ Also read: ⦁ Learn To Protect Your Organization From Spear Phishing.