Use Of Honeypots For The Security Of IoT
December 15, 2019, Kathmandu
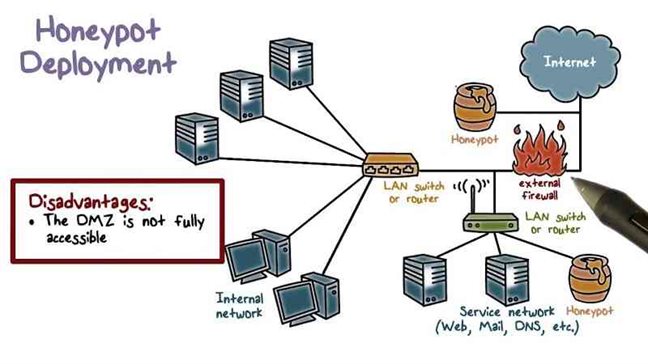
Honeypots can be defined as a computer security mechanism which detects, deflect, counteract attempts at unauthorized use of information systems.
There are basically two types of honeypots based on their use and their level of involvement.
- Production honeypots
- Research honeypots
Production honeypots: it is used to capture only limited information.
Research honeypots: it is used to gather information about the motives of different networks.
Also, based on design, there are three different honeypots:
- Pure honeypots
- High-interaction honeypots
- Low – interaction honeypots
Honeypots are considered as one of the effective methods to track hackers. Recently, Panasonic described the use of internet honeypots and how it helped to secure the devices and data.
Security officials said, “to understand the loT threat landscape and to counter them Panasonic has been using the honeypots”
The process includes, the information collected from honeypots is sent to a sandbox for the analysis. And the system allows Panasonic to collect malware targeting “
This method has helped Panasonic to track 179 million attack and 25,000 malware samples and 4,800 were targeting a lot.
Honeypots are also a low-cost method to enhance your security as honeypots identify unexpected activity. The main target of the honeypot is to scan the network and find out misconfigured and insecure networks and devices and alert the people.
It is one of the best security benefits for organizations and companies to prevent any attack.