What do Security Researchers say on SATAN and Data Breach Rise in Nepal?
April 16, 2020, Kathmandu
Most of you are aware of the latest data breach cases in Nepal. From 50K user’s data leaks from Foodmandu’s database and more than 175K Vianet user’s data leaks to hackers entering Mercantile’s database, we’ve faced frightening situations.
Whether the hacker is Mr. Mugger or he’s ‘Narapichas’, no matter if he’s SATAN too. All these hackers frighten the general public regarding their data safety. So, to provide you more information on Data Breach, we’re presenting you with the exclusive interview with Cyber Security Researches actively working to protect the digital systems in Nepal.
Interview with Alex Dhital, Cyber Security Researcher, and CTF Player:
Q. What do you mean by ‘Data Breach’?
A: Data breach means an incident where an attacker or group of attackers access and publicly disclose the data accessing the critical/unauthorized part of a server to extract the personal and private data of users or the company itself.
Q. What do you think about SATAN? Is he a newbie or an experienced hacker?
A: SATAN is a newbie hacker who is dumping data of various Nepalese sites finding SQL (Structured Query Language) vulnerability injecting queries to drop the tables, columns, and other multiple contents from an unauthorized server. This doesn’t mean he is a professional hacker since this breach looks like he has been using automated tools and scripts which can be found via GitHub and other sources on the internet. If he would have been a professional hacker, he would instead report the company regarding the issue so they can fix it, he would have used his skills in playing CTF, bug bounty (to earn money)and so on rather than causing havoc among the company and the public.
Q. Do you think if he’s a single person or there’s a group behind him?
A: In my opinion, it is probably a single person who is just doing these for attention.
Q. Based on his tweets, most probably he’s a Nepalese. But, do you think he’s doing all these from Nepal or is he residing in the other countries?
A: I believe he is doing all these from Nepal.
Q. In his so-called data of Prabhu Pay, there were duplicated data. Is he leaking data from the servers, or he’s just using the data available anywhere just to grab attention?
A: In Prabhu Money Transfer, he probably might have used the same technique SQL injection to drop the sensitive information from the server, whether from its primary domain fuzzing the potential vectors which were vulnerable to SQLi or one of its subdomains.
Q. In these recent days, the number of data breaches has raised in Nepal. Don’t Nepalese companies invest in security?
A: No, Nepalese company doesn’t invest even its 1% budget in security. As a result, even a newbie like SATAN is dumping their databases.
Q. Are Nepalese companies providing the bounty to bug finders?
A: No, not at all, they aren’t providing the bounty to the bug finders. Soon, Cynical Technology is launching Bugv, a bug bounty platform. I suggest all Nepalese companies partner with it. This will help whitehat hackers and bug hunters to report the vulnerabilities easily and make the system more secure.
Q. If a person finds his data in a breached dump of data, what should he do?
A: If a person finds his data in breached dumps ma if an individual finds his/her data, then they should change their password immediately and enable 2FA (Two Factor Authentication). Similarly, he should avoid providing his information to third party websites in the future.
Q. What do you say about the Cyber Bureau of Nepal? Is it well equipped?
A: I don’t think they are well equipped. Cybersecurity platforms, security training, security-related education, networking related education are not well managed in Nepal. So, they aren’t well equipped. They aren’t well trained in the field of cybersecurity.
Q. As a security researcher, what do you suggest to the companies in Nepal?
A: As a security researcher who also worked in the Onecover Nepal, I suggest Nepalese company invest at least 10% of their total revenue in security. If they do so, they don’t need to worry much about breaches and all. Prevention is better than cure.
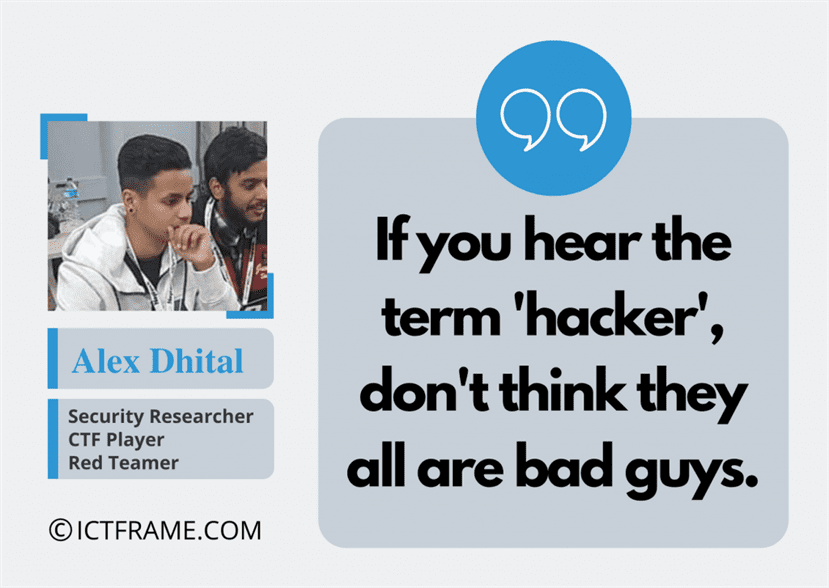
Q. Finally, what would you suggest to the general public?
A: I would like to suggest the general public, if you hear the term ‘hacker’, don’t think they are bad guys. There are white hat hackers who are protecting multinational companies from being infiltrated. And don’t put your personal data/information in any untrusted third-party sources and keep an eye on individual privacy.
Interview with Nabin KC, OWASP Chapter Leader, Nepal:
Q. Please tell us something about the data breach.
A: First, we should understand what data means to an individual, anything that represents some kind of information about any individual can be considered data; it can be digital or written in a thick paper. The data may include anything from general information like name, email, phone number, etc. to credentials like password and credit card information. If anyone gets unauthorized access, we can call it a data breach.
Hackers are not only responsible for data breaches. The data can also be breached from the insider employee with the right access but bad intentions.
Q. What do you say about SATAN? Is he a newbie or an experienced hacker?
A: Rather than going towards the identity rather than we should focus on his deeds in my personal view. Many hackers previously have breached similar Nepalese websites and leaked data multiple times. This is worldwide trend and will happen in future too, but how company have prepared to respond to such breach and handle such incidents reflect company security capability. Well planned response will decrease the breach impact to organization as well to customer. Talking about him, the data he published doesn’t seem to be completely accurate, and few seem to be old, but also, if leakage has happened, we should accept and respond accordingly. He seems to be doing these to get everyone’s attention about his findings but in the wrong way.
The organizations themselves are not able to tell that the leaked data is their real data, what portion of the information is there, which reflects that they don’t have any principle of data collection(Need to know basis). In this scenario, we need to talk on the topic of what the organization is doing to protect it from more data breaches. We need to think actually how can we minimize the impact as it is already a breach.
Q. What are the possible ways person can utilize the Breach data to harm company and customer questions should be brainstorm?
A: General people are also downloading the data. They are searching for their crush details such as home GPS location name and number too, which I recently for my close circle too, this seems fascinating but right.
So, we need to focus on what response is going to be done after any breaches and how the organizations are responding to the incident. We need to focus on the loopholes before searching for the person who harmed it.
Q. What should the organizations do to be protected from data breaches?
A: Talking about the current laws of Nepal, the hacker is punished if the data is breached. If a company is missing basic security things, the organizations should be liable, shouldn’t it? If person puts his money as well some community collected fund in his house and leaves it unlocked and if money is stolen . the first thing community people would ask the money owner is why don’t they lock the house which a basic security, due to this is he lost his money as well community money too.
So, at first, there should be regulation similar to GDPR in foreign countries which govern the company if they had worked on basic security maintenance or it hadn’t. Punishing the hacker is still there but if the company wasn’t maintaining basic security mechanisms, it also should be liable too. If a person gets its data breached from any data holding company, he/she faces the loss and that can’t be compensated. But, other people like him should not face it again. The law should interrogate it.
Since the startups can’t invest much in their security, they can ask for suggestions in security communities without the cost like OWASP NEPAL, PENTESTER NEPAL, as I understand the pain during startup. We are always ready to help. If a person reports the bugs, they should take it seriously and fix it rather than going after who report it. The main thing is, all the organizations should maintain their basic
standards. They can follow the OWASP Application Security Framework during development and do pen-testing on a regular interval basis. They should have information security go side by side with development. As human are the weak points and breach with employee interaction are highest around world. Hence employees information security awareness program should be conducted on regular intervals. One of main thing any organizations should follow to prevent data breaches is monitoring, what we see can only be stopped hence “Monitoring is key for defense”.
Q. What do you say about the Cyber Bureau of Nepal’s action?
A: Cyber Bureau is doing its job well based on the resources they have. They may have thousands of pending cases, and if a situation appears, all the funds shouldn’t be used in the same case. Tracking someone in the digital world is tough. A person living in a foreign country can commit a crime using IP of some other country. The Bureau is doing its work.
They also have find the criminals who committed crime years ago. We can’t judge the efficiency of their work. Based on the current performance, the Bureau is more proactive than before. Different departments have been separated from cybercrime. They’re organizing various awareness programs too, but some things need to be also improved and increase there resources.
Q. Should the government increase its investment in the cybersecurity sector?
A: Yes, that is necessary. Since the government is saying to digitize every sector, they need to focus on security too. They need to increase investment in cybersecurity. If it doesn’t invest in protection, it’ll harm the public. For instance, the database of driving licenses is breached, and a person uses the breached data and creates a license. If he creates an accident and leaves his fake driving license, the next person will get punished. So, the government should allocate a certain percentage of the budget for cybersecurity. Currently, I heard the government has shared people’s license number and citizenship number in some Facebook page of the people who didn’t come to claim for a few months, should we consider it a data leakage too.
Q. If a person finds his data in a breached dump of data, what should he do?
A: Generally, a person can’t completely protect himself from a data breach as it is not all his/her control. What I suggest is using Sudo names (nicknames or some random name ). Almost all websites let users use Sudo names while signing up, excluding banking websites, as they won’t allow it.

Usually, people keep two phones nowadays or have two SIMs. If a person uses two phones, he should use the phone number followed at the primary telephone to receive OTPs. Various applications in smartphones can read the SMS. So, basic feature phones are better to receive OTPs or utilize there two sim, one for financial transactions and other for day to day using web apps like ride-sharing, online delivery, etc.
Similarly, if you use services that require GPS location for any delivery, ride-sharing, don’t provide that exact location of your house instead offer a place you can reach within 2 to 3 minutes. Using different email addresses for various services can reduce the causes after the data breach. We can use our Gmail address by adding as many dots in the middle of our Gmail address. For example, we can use ab.cd@gmail instead of [email protected] for signing up on one website and [email protected] for signing up on the next site. Doing this will reduce the consequences of breach. Current breach data will be utilized by scammers in the future similar to Viber lottery scam now. If scammers have your name, phone number, address, and GPS pinpoint will be easier to scam. This just one of the impact of data Breach there can be many. Hence, we need to be careful about that too.