F5 BIG-IP Found Vulnerable to Kerberos KDC Vulnerability
30th April 2021, Kathmandu
F5 Networks this week released patches to address an authentication bypass vulnerability affecting BIG-IP Access Policy Manager (APM), but fixes are not available for all impacted versions.
“The KDC spoofing vulnerability allows an attacker to bypass Kerberos authentication to the Big-IP Access Policy Manager (APM), bypassing security policies and gaining free access to sensitive workloads.” Said Silver fort researchers Yaron Kassner and Rotem Zach in a report. “In some cases, you can use this to bypass authentication to the Big-IP Management Console.”
Specifically, an attacker could exploit the flaw (tracked as CVE-2021-23008) to bypass Kerberos security and sign into the Big-IP Access Policy Manager, according to researchers at Silver fort. Kerberos is a network authentication protocol that’s designed to provide strong authentication for client/server applications by using secret-key cryptography. In some cases, the bug can be used to bypass authentication to the Big-IP admin console as well, they added.
Along with the release, F5 has released a patch that addresses its weaknesses.
The potential impact could be significant: F5 provides enterprise networking to some of the largest tech companies in the world, including Facebook, Microsoft, and Oracle, as well as to a trove of Fortune 500 companies, including some of the world’s biggest financial institutions and ISPs.
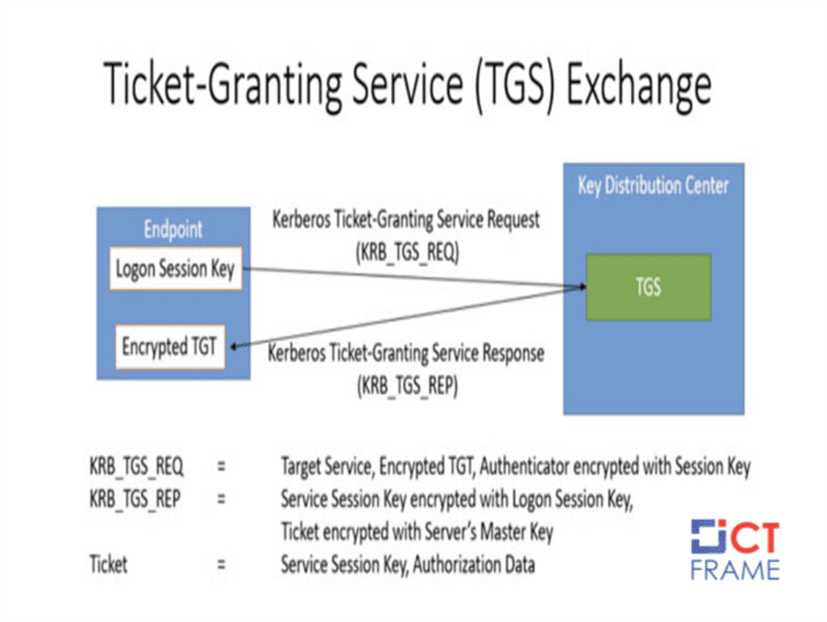
Kerberos is an authentication protocol that relies on the client-server model for mutual authentication and is a Key Distribution Center Kerberos Authentication Server (AS) or Ticket Grant Server in this case — Acts as a repository of shared secret keys for all users, as well as information about which users have access to which services on which network server.
Such attacks typically exploit misconfigurations in Kerberos protocol implementations, and the same applies to F5 BIG-IP as well. Thus, an attacker can create a domain controller with a username identical to the admin’s username and target the flaw to authenticate to BIG-IP even if they do not know the correct password, by hijacking the KDC connection.
“For an APM access policy configured with AD authentication and SSO (single sign-on) agent, if a spoofed credential related to this vulnerability is used, depending on how the back-end system validates the authentication token it receives, access will most likely fail. An APM access policy can also be configured for BIG-IP system authentication. A spoofed credential related to this vulnerability for an administrative user through the APM access policy results in local administrative access,” F5 notes.
BIG-IP APM versions 11.5.2 through 16.0.1 are known to be vulnerable. Fixes were included in BIG-IP APM versions 12.1.6, 13.1.4, 14.1.4, and 15.1.3, but no patches are available for the 11.x and 16.x branches.
As for mitigations, F5, which also credits Thierry Van Steirteg hem from Exclusive Networks for reporting the vulnerability, suggests enabling multi-factor authentication (MFA), or host-level authentication.
This week, the company also released patches for a medium-severity vulnerability in BIG-IP APM (CVE-2021-23016) that could be abused to bypass internal restrictions and retrieve static content stored within APM.