Android Users Exposed To Remote Attacks Due To Flaws in Samsung Phones
13th August 2020, Kathmandu
New research has revealed a serious security vulnerability in the ‘Find My Mobile’ – an Android app that comes pre-installed on most Samsung smartphones.
Char49, a Portugal-based cybersecurity provider, revealed its findings on the android app at the DEF CON conference last week.
The research suggests that this flaw had the potential to allow remote attackers to track victim’s real-time location and monitor their call activities.
In addition, the attackers could even check messages and delete data from the phone.
According to Char49’s Pedro Umbelino, attackers could cause serious privacy implications via IMEI and location tracking. Moreover, it could even cause catastrophic impacts such as the permanent denial of service via phone lock and factory reset.
“This attack was tested successfully on different devices (Samsung Galaxy S7, S8, and S9+”, the report suggests.
Samsung addressed these vulnerabilities after flagging the exploit as a “high impact vulnerability”.
Vulnerabilities… More than One?
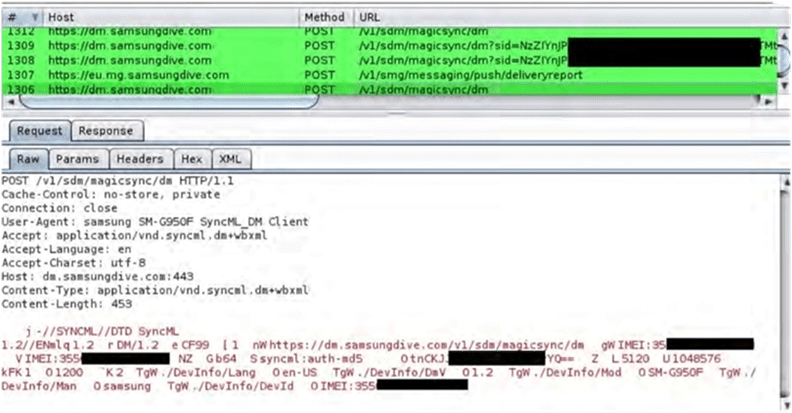
According to Char49, there were a total of 4 different vulnerabilities in the Find My Phone app. In fact, attackers could’ve easily exploited the targeted device using a malicious app.
The app checks for a specific file on the phone’s SD card (“/mnt/sdcard/fmm.prop”) in order to load a URL (“mg.URL”). Thus, this allows a malicious app to create this file which a bad actor can use to potentially hack the communications with the server.
In this way, the attacker can get access to several personal information about the user.
Furthermore, the malicious app installed on the device uses an exploit chain that leverages two different unprotected broadcast receivers. These would allow redirecting commands intended for Samsung’s servers from the Find My Mobile app to a different server under the attacker’s control.
In fact, the malicious server later also forwards the request to the legitimate server and retrieves the response. However, that doesn’t happen before it injects its own commands in the server responses.
Consequently, the attackers now have full control over the flawed Samsung device.
And ironically, an app that’s supposed to safeguard users against information loss becomes the villain. The flaw basically defeats the app’s very purpose.
Suggested Reads
- Cybersecurity Landscape is Changing and It is Inevitable
- Apple iPhone 11 Series Ships With A Security Flaw: Here Are The Details
- Huawei Overtaken Samsung to Become the Largest Smartphone Retailer