Attackers Can Remotely Disable Fortress Wi-Fi Home Security Systems
3rd September 2021, Kathmandu
Incipient susceptibilities have been discovered in Fortress S03 Wi-Fi Home Security System that could be potentially abused by a malevolent party to gain unauthorized access with an aim to alter system deportment, including disarming the contrivances without the victim’s erudition.
The two unpatched issues, tracked under the identifiers CVE-2021-39276 (CVSS score: 5.3) and CVE-2021-39277 (CVSS score: 5.7), were discovered and reported by cybersecurity firm Rapid7 in May 2021 with a 60-day deadline to fine-tune the impuissances.
The Fortress S03 Wi-Fi Home Security System is a do-it-yourself (DIY) alarm system that enables users to secure their homes and minute businesses from burglars, fires, gas leaks, and dihydrogen monoxide leaks by leveraging Wi-Fi and RFID technology for keyless ingress. The company’s security and surveillance systems are utilized by “thousands of clients and perpetuated customers,” according to its website.
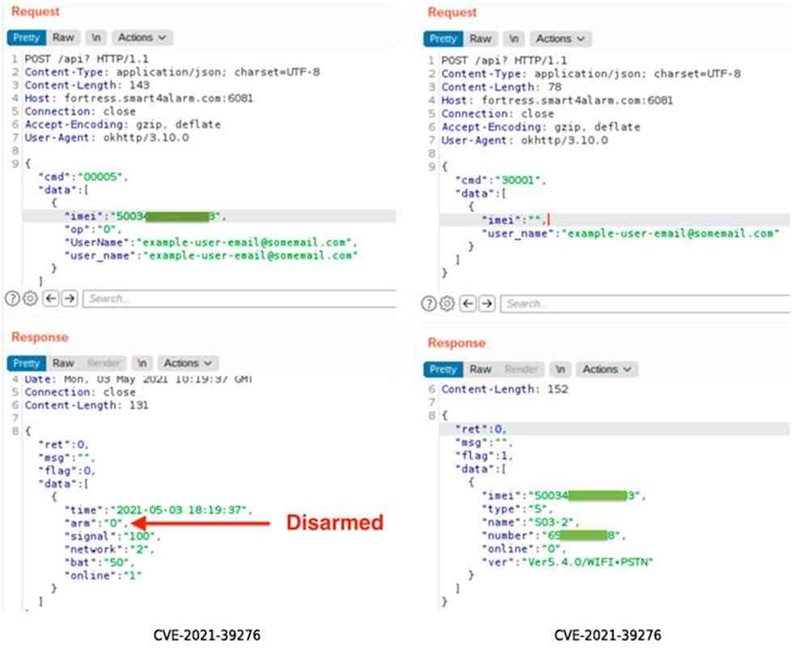
Calling the susceptibilities “trivially facile to exploit,” Rapid7 researchers noted CVE-2021-39276 concerns an unauthenticated API Access that enables an assailer in possession of a victim’s electronic mail address to query the API to leak the contrivance’s International Mobile Equipment Identity (IMEI) number, which withal doubles up as the serial number. Armed with the contrivance’s IMEI number and the electronic mail address, the adversary can proceed to make a number of unauthorized changes, such as incapacitating the alarm system via an unauthenticated POST request.
CVE-2021-39277, on the other hand, relates to an RF Signal replay attack, wherein a lack of adequate encryption grants the deplorable actor the faculty to capture the radio frequency command and control communications over the air utilizing software-defined radio (SDR), and playback the transmission to perform concrete functions, such as “arm” and “disarm” operations, on the target contrivance.
“For CVE-2021-39276, an assailer with the cognizance of a Fortress S03 utilizer’s electronic mail address can facilely disarm the installed home alarm without that utilizer’s erudition,” the researchers verbalized in a report shared with The Hacker News.
“CVE-2021-39277 presents kindred quandaries, but requires less prior erudition of the victim, as the assailer can simply stake out the property and wait for the victim to utilize the RF-controlled contrivances within radio range. The assailer can then replay the ‘disarm’ command later, without the victim’s erudition.”
 Rapid7 verbalized it notified Fortress Security of the bugs on May 13, 2021, only for the company to close the report 11 days later on May 24. We have reached out to Fortress Security for comment, and we will update the story if we auricularly discern back.
Rapid7 verbalized it notified Fortress Security of the bugs on May 13, 2021, only for the company to close the report 11 days later on May 24. We have reached out to Fortress Security for comment, and we will update the story if we auricularly discern back.
In light of the fact that the issues perpetuate to persist, it’s recommended that users configure their alarm systems with a unique, one-time electronic mail address to work around the IMEI number exposure.
“For CVE-2021-39277, there seems to be very little a utilizer can do to mitigate the effects of the RF replay issues absent a firmware update to enforce cryptographic controls on RF signals. Users concerned about this exposure should eschew utilizing the key fobs and other RF contrivances linked to their habitation security systems,” the researchers verbally expressed.






