Cloud Computing Security Vulnerabilities and What to Do
7th May 2021, Kathmandu
Cloud vulnerability (Cloud Security Monitoring - Reduce Hours of Vulnerability)
Many organizations are continuously trying to establish on cloud nowadays, which is one of the most important reasons why...
Nepal DDOS Attack Trends & How You Should Respond
5th May 2021, Kathmandu
Digital Network Solutions is all set to organize DDOS Attack trends in Nepal and How we should respond to the webinar on 12th May 2021 from 11 a.m.
The...
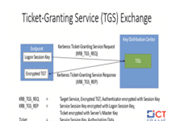
F5 BIG-IP Found Vulnerable to Kerberos KDC Vulnerability
30th April 2021, Kathmandu
F5 Networks this week released patches to address an authentication bypass vulnerability affecting BIG-IP Access Policy Manager (APM), but fixes are not available for all impacted versions.
“The KDC...
Case Against REDDIT For Not Removing Child Sexual Abuse Material
27th April 2021, Kathmandu
One female has filed a case against Reddit. She blamed her ex-boyfriend for posting her 16 years old porned photo time and again.
The issue applies to controversial measures...
Chrome Zero-Day Exploit Posted on Twitter
27th April 2021, Kathmandu
The term “Zero-day” is an imaginative time, as this type of cyberattack happens in less than a day since the awareness of the security flaw. Thereby, not giving...
Zero Trust: The Mobile Dimension
27th April 2021, Kathmandu
Hank Schless, senior security options manager at Lookout, discusses how to secure remote performing through mobile gadgets. Hank Schless, is senior security answers manager at Lookout.
Soon after embarking...
Saint Bot – A New Malware Downloader Spotted
25th April 2021, Kathmandu
With the rapid technological advancement in the cybercrime realm, attackers are coming up with new ways of quickly developing and deploying sophisticated malware. Recently, security researchers identified a...
THE smart TV tech loophole allowed miscreants to view private YouTube videos
25th April 2021, Kathmandu
Smart TV Tech Loophole Allowed Miscreants to View Private YouTube Videos. Security researcher earned a $6,000 bug bounty after uncovering a set of web security flaws that allowed attackers to...
Apple macOS TextEdit Parsing Flaw leaked local Files via Dangling
25th April 2021, Kathmandu
Apple macOS TextEdit parsing flaw leaked local files via dangling markup injection
UPDATED A vulnerability in macOS allowed attackers to execute malicious HTML on TXT files which, if opened by...
Vulnerabilities in Single Sign-On Services Could be Abused to Bypass Authentication
25th April 2021, Kathmandu
Vulnerabilities in Single Sign-On services could be abused to bypass authentication controls
A category of vulnerability detected in a number of Single Signal-On (SSO) companies may enable attackers to...
Cyber Warfare: The Battle Tact of the Digital Age
25th April 2021, Kathmandu
As cyberattacks continue to bypass even the tightest cybersecurity measures, the impact on consumers is reaching new heights – and investors are feeling the pressure
Cyberwarfare is a computer-...
Is Automated Vulnerability Remediation the Answer?
25th April 2021, Kathmandu
Executing a well-run vulnerability management program is essential to protecting against data breaches and ensuring the availability of your IT infrastructure. What is your mean time to remediate...
CEH and Four Other EC-Council Certification Exams Earn College Credit
25th April 2021, Kathmandu
EC-Council is pleased to announce five certifications that recently received approval from the American Council on Education (ACE). This is a major step to help jump-start college careers as well as...
Prometei Botnet Exploiting Unpatched Microsoft Exchange Servers
25th April 2021, Kathmandu
Attackers are exploiting the ProxyLogon Microsoft Exchange Server flaws to co-opt vulnerable machines to a cryptocurrency botnet named Prometei, according to new research.
"Prometei exploits the recently disclosed Microsoft...
Hackers Exploit VPN to Deploy SUPERNOVA malware on SolarWinds Orion
25th April 2021, Kathmandu
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has disclosed details of a new advanced persistent threat (APT) that's leveraging the Supernova backdoor to compromise SolarWinds Orion installations...
Cost of Account Unlocks, and Password Resets Add Up
There are many labor-intensive tasks that the IT service desk carries out on a daily basis. None as tedious and costly is resetting passwords.
Modern IT service desks spend a significant amount...
5 Fundamental But Effective IoT Device Security Controls
25th April 2021, Kathmandu
Matt Dunn, the associate managing director for cyber-risk at Kroll, discusses how to keep networks safe from insecure IoT devices.
As the pandemic continues to fuel the shift to...
Cyberthreats Still Loom Over E-learning Platforms
24th April 2021, Kathmandu
E-learning or electronic learning, Is the delivery of learning and training through digital resources or devices such as computers, tablets, and even cellular phones that are connected to...
API Risks: What are They and How to Manage Them
24th April 2021, Kathmandu
API security risks are a common problem in today’s cyber world. Unfortunately, cyberattacks have become an everyday word in today’s vernacular. Like any software, APIs can be compromised...
Everything You Need to Know About the Malvertising Mayhem
Everything You Need to Know About the Malvertising Mayhem
What is Malvertising?
Malvertising is a pet name for malware that’s delivered through online advertising techniques. The ads look authentic. Often, legitimate third-party marketing companies distribute...
Solarwinds Hack Orchestrated by Russia’s SVR, Claims U.S. and U.K.
24th April 2021, Kathmandu
Hackers working for the Russian foreign intelligence service are behind the SolarWinds attack, cyber-espionage campaigns targeting COVID-19 research facilities, and more, according to the United States and the...
Mount Locker Ransomware Aggressively Changes Up Tactics
24th April 2021, Kathmandu
Mount Locker group first announced their ransomware-as-a-service offering in the second half of 2020, and attacks attributed to the variant have been on the rise since. In early...
4 Innovative Ways Cyberattackers Hunt for Security Bugs
24th April 2021, Kathmandu
David “moose” Wolpoff, co-founder and CTO at Randori, talks about lesser-known hacking paths, including unresolved “fixme” flags in developer support groups.
Blue teamers are in a constant battle against...
Telegram Platform Abused in ‘ToxicEye’ Malware Campaigns
23rd April 2021, Kathmandu
Hackers are leveraging the popular Telegram messaging app by embedding its code inside a remote access trojan (RAT) dubbed ToxicEye, new research has found. A victim’s computer infected...
FBI Removes Malicious Web Shells From Microsoft Exchange Servers
23 April 2021, Kathmandu
Federal law enforcement, toting a court order, excised malicious web shells from hundreds of exposed servers in the U.S. compromised by the fleecing of zero-day flaws in Microsoft...
Has Babuk Ransomware Gang Attempted a Slam Dunk on Houston Rockets?
22nd April 2021, Kathmandu
The Houston Rockets of the National Basketball Association are investigating a cyber-attack against their networks from a relatively new ransomware group that claims to have stolen internal business data....
What is DDOS and how can I Better Defend My Business Against this Threat?
22 April 2021, Kathmandu
With every step that our world takes into the digital age, the risk of cyber attack becomes a more and more daunting threat. Of the many types of cyberattacks,...
Behind the Great Firewall: Chinese Cyber-espionage Adapts
19th April 2021, Kathmandu
Behind the Great Firewall: Chinese cyber-espionage adapts to the post-Covid world with stealthier attacks
Threat intelligence experts quizzed by The Daily Swig said that Chinese state-sponsored attackers are at the forefront of developing...
Pressure Grows on Valve to Unplug Steam Gaming Platform Vulnerabilities
18th April 2021, Kathmandu
Stress is rising on video games writer Valve after two units of safety researchers got here ahead with complaints that it has been sluggish at resolving safety flaws...
New GitHub Repo Details Legal Threats and Risks Faced by Ethical Hackers
18th April 2021, Kathmandu
A new GitHub repository has been created to document and track the times when vulnerability disclosure has gone sour.
The Research Threats project details historical legal battles between researchers and the target organizations...