What are Supply Chain Attacks by cybersecurity?
28th August 2021, Kathmandu
Today, a growing number of hackers are adopting sophisticated implements and techniques to assail a company’s Supply Chain Management and wreak havoc in business operations.
In today’s evolving digital...
How to Update Web Browsers for Secure Browsing
10th May 2021, Kathmandu
The World Wide Web accessing software application also known as web browsers or simply “browser” is used to access and view websites through internet. Some of well-known browsers...
4 Innovative Ways Cyberattackers Hunt for Security Bugs
24th April 2021, Kathmandu
David “moose” Wolpoff, co-founder and CTO at Randori, talks about lesser-known hacking paths, including unresolved “fixme” flags in developer support groups.
Blue teamers are in a constant battle against...
Hackers Exploit VPN to Deploy SUPERNOVA malware on SolarWinds Orion
25th April 2021, Kathmandu
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has disclosed details of a new advanced persistent threat (APT) that's leveraging the Supernova backdoor to compromise SolarWinds Orion installations...
Scam Links Circulating in the Name of Bhatbhateni Supermarket
21st October 2022, Kathmandu
A scam link has been circulating in the name of Bhatbhateni Supermarket. Scam links are being spread on social networking sites and the internet saying that a new...
Cost of Account Unlocks, and Password Resets Add Up
There are many labor-intensive tasks that the IT service desk carries out on a daily basis. None as tedious and costly is resetting passwords.
Modern IT service desks spend a significant amount...
Morgan Stanley Discloses Data Breach After the Hack of a Third-party Vendor
13th July 2021, Kathmandu
The Investment banking firm Morgan Stanley has disclosed a knowledge breach after threat actors have compromised the Accellion FTA server of the third-party vendor Guidehouse.
The company has offices...
Stranger’s Messages Threatens Cyber Security
The use of social networks is increasing in the same way as cyber attacks are burgeoning.
To discover someone’s data has been a small deal at the present scenario. We should apply...
Facebook Caught Iranian Spies
23 July 2021, Kathmandu
Facebook revealed that it tracked and partly disrupted a cyber espionage campaign launched by Iranian hackers, collectively mentioned as Tortoiseshell or Imperial Kitten.
On Thursday, Facebook said that it had taken...
10 Most Powerful Hacking Techniques You Must Know
15th May 2021, Kathmandu
Hacking is the unauthorized access to or control over computer network security systems for some illicit purpose. Hacking means compromising computer systems, personal accounts, computer networks, or digital...
Cyber Attack: New Dangerous Version Of Wanna Cry Ransomware
Recently, the internet faced a massive attack which is believed to be the most massive ransom-ware delivery campaign to date. The ransom-ware campaign hit computer systems of hundreds of private companies...
MUSIC NEPAL Most Subscribed YouTube Channel of Nepal Hack
4th July 2022, Kathmandu
The YouTube channel of Music Nepal has been hacked. Music Nepal has the most subscribers on YouTube in Nepal.
The channel has been renamed Tesla Live after it was...
THE smart TV tech loophole allowed miscreants to view private YouTube videos
25th April 2021, Kathmandu
Smart TV Tech Loophole Allowed Miscreants to View Private YouTube Videos. Security researcher earned a $6,000 bug bounty after uncovering a set of web security flaws that allowed attackers to...
Threat to Google Chrome Passwords: NPM Malware
24th July 2021, Kathmandu
Threat to Google Chrome Passwords: NPM Malware. NPM malware was found exploiting passwords of Google Chrome.
It is a known incontrovertible fact that organizations and individuals should protect publicly...
Win10 Admin Rights Tossed Off by yet another Plug-In
28th August 2021, Kathmandu
Then again, you don’t even require the authentic contrivance, in this case, a SteelSeries peripheral since emulation works just fine to launch with full SYSTEM rights.
It’s not just...
Microsoft Launches a National Campaign to Support Community Colleges in their Efforts to Grow...
31st October 2021, Kathmandu
The United States is facing a cybersecurity skills shortage: Microsoft has launched a national campaign to support community colleges in their efforts to grow their cybersecurity workforce.
The last...
Using “Signal” For Encrypted Chats, You Shouldn’t Skip Its Next Update
Through signals, many attackers are targeting your devices, and it directly or indirectly affects to your system as well so let’s know how the message would impact to your system.
The whistleblower...
APT Used a FatPipe VPN Zero-day Exploit for Six Months
20th November 2021, Kathmandu
ACCORDING TO THE FBI'S FLASH NOTICE, an APT has been using the issue to compromise FatPipe router clustering and load balancer products to breach targets' networks.
According to the...
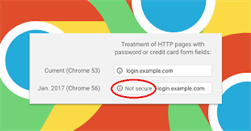
Google Chrome To Label Sensitive HTTP Pages As “Not Secure”
Google is going to give us the incredible gift for this Upcoming New Year 2017 to secure our privacy and security. Now I would tell you what that is and how...
A Tech One Global Event On Cyber Security And Data Privacy
Compliance and Protection: A Tech One Global Event on Cyber Security and Data Privacy
June 2017, Discovery Primea, Makati —Tech One Global has launched an event called "Cybersecurity and Data Privacy" together with...
MSPs, Hybrid Workers and Connected Cars Face Cyber-Threat Onslaught in 2023
15th December 2022, Kathmandu
Trend Micro Security Predictions for 2023, The report warns that threat actors will ramp up attacks targeting security blind spots in the home office, software supply chain, and cloud...
Trend Micro Named a Leader in Endpoint Security
30th October 2023, Kathmandu
Trend Micro today announced its recognition by Forrester as a Leader in endpoint security. The independent market analysis states that "Trend Micro is the veteran that leads with...
Publicity around the hack of Mr. Zuckerberg’s accounts
People, not computers, create computer threats. Computer hackers are unauthorized users who break into PC systems to steal, change or destroy the information and data. Anyone who uses a computer connected...
Public Notice For Selection of Information Security Consulting Firms
30 December 2020, Kathmandu
Nepal Telecommunications Authority Announced Public Notice For Selection of Information Security Consulting Firms. To get enlisted in a roster of NTA as IS Auditor/Cloud Auditor
(First date of publication...
The Authentic Way to Get Geolocation of any Contrivance With Kali Linux
10th October 2021, Kathmandu
In this article, we are going to learn how to locate any contrivance through Kali Linux utilizing implements. Here, I am utilizing nGrok, sneaker, and IP locator implements....
Vianet Was Released Without any action in case of Hacking Customer Data
17th Feb 2021, Kathmandu
Vianet Communications, an Internet service provider was found to be free of regulatory consumer data theft.
Last year, the data of Vianet's customers was made public by hackers. Sensitive...
Imperva® Opens Network and Security Operations Centre in Singapore to Better Support APJ and...
12th April 2023, Kathmandu
Positioning itself as the cybersecurity leader in the Asia Pacific and Japan (APJ) that protects critical applications, APIs, and data, anywhere at scale, Imperva, Inc., (@Imperva) unveils a...
US Warns To Hacking Threat To Interbank Payment System
US officials have recently issued a warning to banking institutions about potential cyber-attacks linked to the interbank messaging system. This statement came just two weeks after the FBI’s cautionary notice to...
Apple Releases iOS 15.0.2 Security Update to Fix IOMFB Bug
16th October 2021, Kathmandu
Mac has delivered a security update iOS 15.0.2 and iPad OS 15.0.2 to fix a zero-day weakness that is effectively taken advantage of in assaults focusing on iPhones...
Cloud Computing Security Vulnerabilities and What to Do
7th May 2021, Kathmandu
Cloud vulnerability (Cloud Security Monitoring - Reduce Hours of Vulnerability)
Many organizations are continuously trying to establish on cloud nowadays, which is one of the most important reasons why...