Protect Database From Security Threats, Secure IT
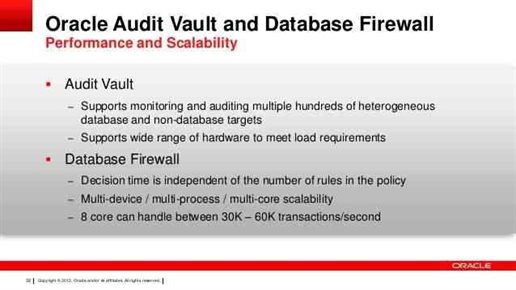
The database security deals with the use of wide ranges of information security prevention to secure databases that generally include the data, the database systems, database applications or stored functions, the...
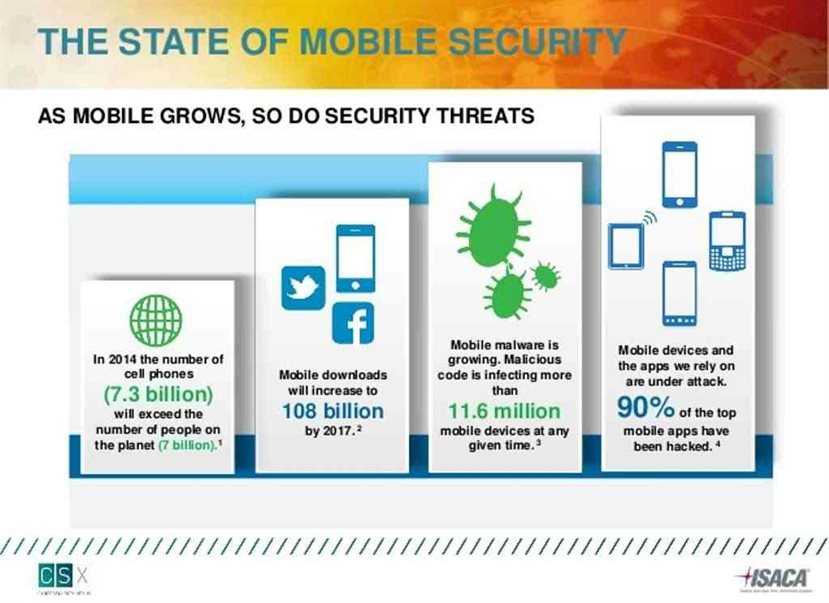
Mobile Security Threats Are Exploding
News by- Dr. Ramhari Subedi
As mobile phones are becoming very useful and very popular, threats level have also increased by 40%. We barely pay attention to updating software of mobile apps,...
Global Risk Management Survey Highlights Cyber Attack For Organization
23rd November 2023, Kathmandu
Aon plc, a leading global professional services firm, has announced the results of its 2023 Global Risk Management Survey, which gathered input from almost 3,000 risk managers, c-suite...
Google patches Chrome zero-day, eighth one in 2021
19th July 2021, Kathmandu
Eight security vulnerabilities, including a high severity zero-day flaw exploited in the wild, are inscribed by Google Chrome.
Chrome’s new version (91.0.4472.164) has been released for Windows, Mac, and...
Apple Release Emergency Security Patch IOS 9.3.5
1st September 2016, Kathmandu
Apple was bound to release iOS 9.3.5 update “Emergency” Patch for apple products like iPhone, iPad, etc. after advanced spyware targets the iPhone used by a renowned UAE...
Nepal Rastra Bank Warns the Hackers Threatening Nepal’s Banking System
22 July 2021, Kathmandu
News that Nepal's banking system has been 'hacked' since Wednesday has caused panic. Mentioning the names of 16 banks, the message that the system has been "compromised" and...
38 Million Records Exposed from Microsoft Power Apps of Dozens of Organizations
25th August 2021, Kathmandu
More than 38 million records from 47 different entities that believe Microsoft's Potency Apps portals platform were inadvertently left exposed online, bringing into sharp focus an "incipient vector...
Research Highlights Cyber Security’s Underestimated Role as a Business and Revenue-enabler
22nd March 2023, Kathmandu
Trend Micro, a global cybersecurity leader, today released new research* revealing that while global organizations plan to increase cybersecurity budgets in 2023, business leaders hold conflicting views on...
How to Use VPN on Windows: A Complete Step-by-step Guide
26th September 2020, Kathmandu
Using a VPN has become a necessity when it comes to surfing the internet securely. In fact, it isn’t only about getting access to some restricted sites as...
The Importance Of A Security Culture Across The Institution
A significant impact is made by the employee's behavior to information security in organizations. The culture concept can help different parts of the organization that concerns about information security within the...
ChildSafeNet Marks 5 Years of Online Safety for Children
14th June 2023, Kathmandu
ChildSafeNet, an organization dedicated to making the internet safer for children and young people, is proud to announce the successful completion of its five-year journey.
Since its unofficial inception...
ThreatNix Appends IS Audit Service
ThreatNix a company which is specialized in providing cyber security related service has added a new amenity in its working list. The company has started the service of IS audit.
An information technology...
Apple Releases iOS 15.0.2 Security Update to Fix IOMFB Bug
16th October 2021, Kathmandu
Mac has delivered a security update iOS 15.0.2 and iPad OS 15.0.2 to fix a zero-day weakness that is effectively taken advantage of in assaults focusing on iPhones...
Letter from Assistant Professor of Cyber Security Dr. Ramhari Subedi
Hello everyone,
Cyber Security International (CSI) is based out of Washington DC USA. CSI mission is to raise awareness of emerging cyber threats to teenagers’, parent, students, officials, social activists, leaders, lawmakers,...
How To Find Fake Facebook Accounts ? Bhaskar Bhatt
How to identify a fake user account on the Facebook following are some tips:
1. The statement was made recently 2015, 2016.
2. The report has no history published for earlier years, but...
Women in Big Data-Nepal To Host Belt Your Data For Data Enthusiasts
17th July 2020, Kathmandu
Women in Big Data-Nepal is all set to organize a Virtual Panel Discussion on the topic ‘Belt Your Data’ on 19 July, Sunday. The event aims to share...
NIC Asia Bank Spearheads Financial Security Amidst Escalating Cyber Risks
31st March 2024, Kathmandu
In today's era of technological advancement and digitalization, safeguarding financial security has become paramount.
NIC Asia Bank stands at the forefront, championing the cause of protecting its customers amidst...
GitHub Prepares to Move Beyond Passwords
13th May 2021, Kathmandu
Github, a platform that provides internet hosting for software development and distributed version control, uses Git over SSH as supporting security keys.
Kevin Jones, the Github security engineer, said...
Fake Netflix App on Google Play Spreads Malware via Whatsapp
11th April 2021, Kathmandu
A fake application on google play, claiming to allow users to view Netflix content from all over the world, was spreading malware through WhatsApp messages, according to researchers...
E-Marketing Data Exposed Online From Unsecured MongoDB
11M Records of E-Marketing Data Exposed Online From Unsecured MongoDB Instance. With the running time, there has been development in almost everything. Comparatively, the growth in the technology world is extreme. Along...
Cyber Threats: An Interactive Virtual Training for Financial Institutions in Nepal
5 March 2021, Kathmandu
CRDF Global is convening a web-based training to protect against state-sponsored cyber-attacks on financial institutions, such as attacks from the Democratic People's Republic of Korea (DPRK) on March 18 and 19...
Researchers Detail Modus Operandi of Shiny Hunters Cyber Crime Group
25th August 2021, Kathmandu
ShinyHunters, a notorious cybercriminal underground group that's been on a knowledge breach spree since last year, has been optically canvassed probing companies' GitHub repository ASCII text file for susceptibilities which will be abused to...
Nepal CERT leads the Chiranjibi Adhikari
Information Security Response Team Nepal (NPCERT) is a team of Information Security experts formed to address the urgent need for the protection of national information and growing cybersecurity threat in Nepal....
How to Check if Your iPhone is Hacked?
23rd March 2023, Kathmandu
iPhones have become an essential aspect of our daily lives. We use them for important activities like shopping online and storing private data. With features like Apple Pay,...
Security And Privacy Issues In E-Government, Pavan Duggal
Mr. Pavan Duggal is the President from India has been working on Cyberlaw Asia.Net on Security Issues of E-Government Applications. He is the pioneering of Cyberlaw and the Director of the...
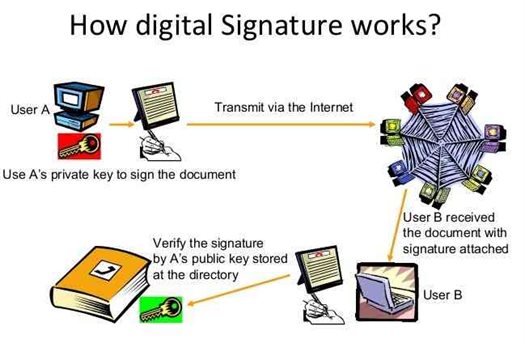
How To Use DSC For The First Time In Your PC ?
Steps for Using Token from Nepal Certifying Company
Insert the provided token and wait for the dialogue box to appear.
Click on the Open folders to view files, three directories Mac/Linux/Windows will be displayed.
...
Common Facebook Crimes In Nepal
For better or Worse, the Internet has become an integral part of life all over the world. On the negative side, interconnectivity created new breeds of crime, such as cyberstalking and...
Magento Core Malware Steals Payment Card Details
Cybercriminals are targeting websites running the Magento platform to inject them with code that can steal credit card data and infect visitors with malware, Flashpoint reports.
A new payment card stealing campaign...
What Is Information Security Policy ? Cyber Security Law And Policy
Information Security Policy is a collection of policies implemented by an organization to make sure that all the information technology users within the grasp of the organization or its branches stay...
New Trojan ‘‘Android.Cynos.7.origin’’ Infects 9Mn Android Devices
26th November 2021, Kathmandu
Security researchers from Doctor Web have found another Trojan that has infected over 9.3 million Android devices.
The Trojan, named "Android.Cynos.7.origin," is another type of malware that makes itself...