Turkish Hacktivists Targets Social Media Account Of Journalists
Recently, the Twitter account of NBC national correspondent Peter Alexander appears to have been hijacked by hackers claiming to represent Turkey’s “cyber army.”
For at least a half-hour Sunday morning, Alexander’s Twitter...
Android Users Exposed To Remote Attacks Due To Flaws in Samsung Phones
13th August 2020, Kathmandu
New research has revealed a serious security vulnerability in the ‘Find My Mobile’ - an Android app that comes pre-installed on most Samsung smartphones.
Char49, a Portugal-based cybersecurity provider,...
Tiktok Tracked Users’ Data For Over A Year
14th August 2020, Kathmandu
According to the Wall Street Journal, Tiktok tracked Android users’ data for over a year until November 2019. This is yet another blow for tiktok in the recent...
Russia’s Critical Sectors Under APT Group ChamelGang’s Radar
10th October 2021, Kathmandu
The assault vector of Russian state-supported progressed diligent danger (APT) assailants is stretched out across different nations. Various cybercriminal bunches from Russia have designated a few worldwide basic...
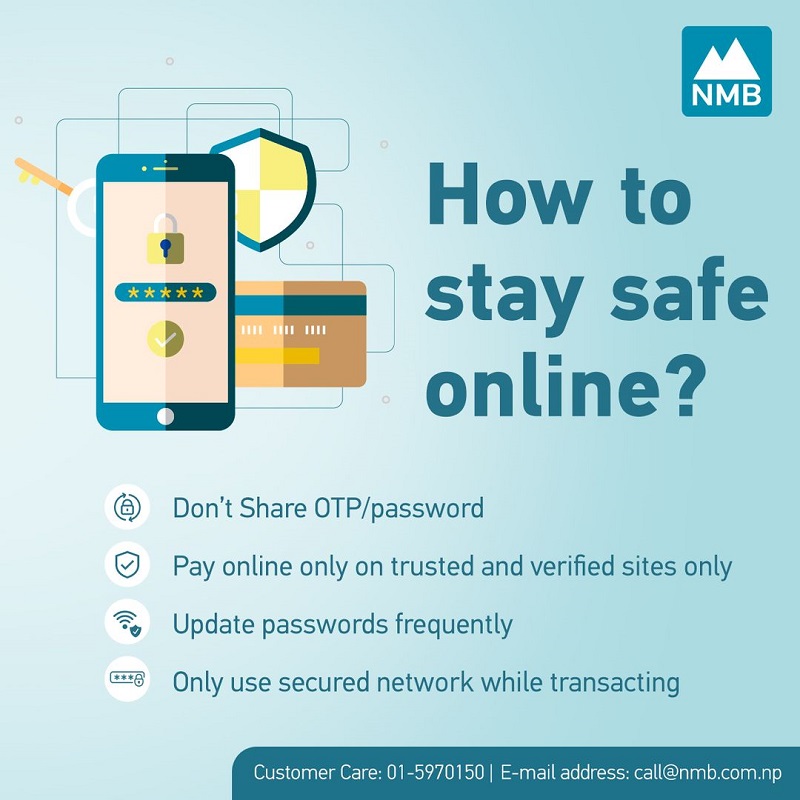
NMB Bank Limited Presents: How to Stay Safe Online?
18th August 2023, Kathmandu
Mastering Online Safety: Expert Tips to Safeguard Your Internet Presence Secure Your Digital World with NMB Bank Limited Presents.
In today's interconnected world, safeguarding your online presence has never...
7 Most Common Facebook Crimes In Nepal
For better or Worse, the Internet has become an integral part of life all over the world. On the negative side, interconnectivity created new breeds of crime, such as cyberstalking and...
Dedicated Cybersecurity Company From Nepal
Kathmandu, March 23
Cybersecurity is the practice of defending systems, networks, servers, and programs from digital malicious attacks. The term cybersecurity can also be replaced with IT Security or Electronic Information Security....
Hacking of IATA and Server Systems Leads to Millions of Airline Tickets
31st May 2023, Kathmandu
The hacking incidents that have targeted the Nepali travel industry professionals have raised serious concerns about the security and reliability of the International Air Transport Association (IATA) and...
How Does Pegasus Software Hack Phones?
22 July 2021, Kathmandu
Pegasus software is spyware developed by an Israeli tech company called NSO Group. This group is especially known for making cyber weapons.
Pegasus is a highly sophisticated surveillance software...
India Bans 59 Chinese Apps Including TikTok
30th June 2020, Kathmandu
The Indian Government on Monday evening decided to ban 59 apps developed by Chinese firms saying their activities threaten the sovereignty and integrity of the country.
The list of...
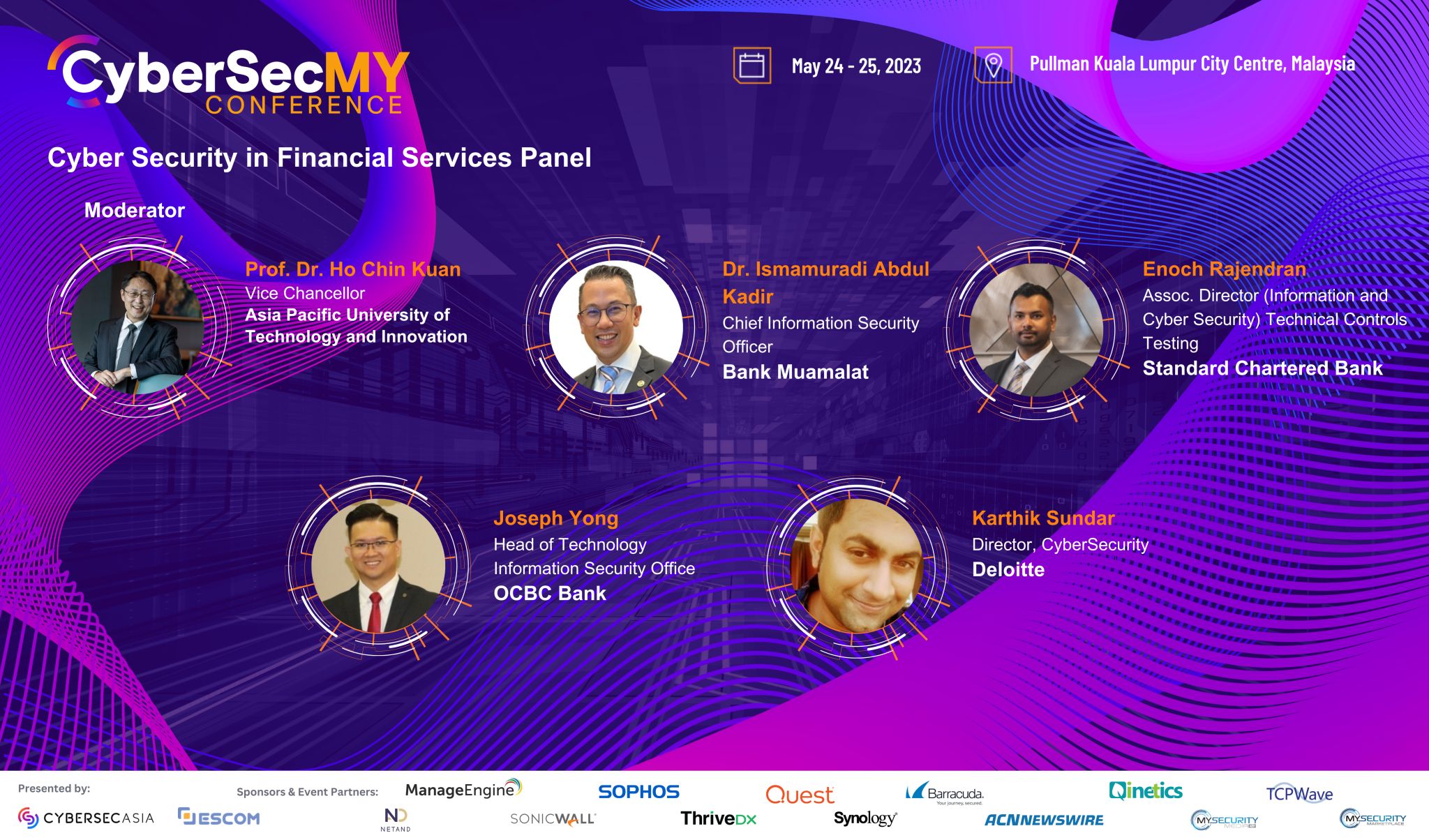
Cybersecurity Conference In Kuala Lumpur City Centre Malaysia
22nd May 2023, Kathmandu
CyberSecMalaysia Conference 2023 is organizing the theme of Strengthening Cybersecurity Landscape in Malaysia Emerging Technologies for Cybersecurity in 2023 at Pullman Kuala Lumpur City Centre, Malaysia.
CyberSecMalaysia Conference is...
New York City Law Department Hit by a Cyber-attack
10th June 2021, Kathmandu
A cyber-attack is any offensive maneuver that targets data, computers, infrastructures, computer networks, or personal computer devices. In other words, an attacker is a person or process that attempts...
87% Of Android Phones Are Vulnerable To Hackers
Smartphone, an ancient but good friend, is the thing that we always keep on carrying. Wherever we go, with whomever we go in any new or old destination we always bring...
MUSIC NEPAL Most Subscribed YouTube Channel of Nepal Hack
4th July 2022, Kathmandu
The YouTube channel of Music Nepal has been hacked. Music Nepal has the most subscribers on YouTube in Nepal.
The channel has been renamed Tesla Live after it was...
Second Cyberattack at Iran’s Transport Ministry
13th July 2021, Kathmandu
Iran's Transport Ministry has affirmed that its official website was hit by a cyberattack, that led the portal page of the Ministry and its affiliated pages to go...
U.S. Cyber Command Warns of Ongoing Attacks Exploiting Atlassian Confluence Flaw
5th September 2021, Kathmandu
The U.S. Cyber Command on Friday admonished of perpetual mass exploitation endeavors within the wild targeting a now-patched critical security susceptibility affecting Atlassian Confluence deployments that would be abused by unauthenticated assailants to...
LockFile Ransomware Bypasses Protection Using Intermittent File Encryption
29th August 2021, Kathmandu
An incipient ransomware family that emerged last month comes with its own bag of artifices to bypass ransomware aegis by leveraging a novel technique called "intermittent encryption."
Called LockFile,...
Anonymous User Leaks 500 People’s Private Information on Twitter
16th May 2020, Kathmandu
An anonymous user that goes by the username @LKhyah on Twitter has leaked data of 500 people through Twitter. The person has posted a link to Medium that...
Learn How Ransomware Works And How To Avoid It
1st March 2016, Kathmandu
Ransom-ware is one of the computer virus or malware that locks the computers files and demand money to return their records.
It is one of the growing threads for...
ICT For Good Governance, Electronic Transaction Rules 2064
Digital Signature and Certificate (DSC) has been issued to inform all that on December 2, 2015, Honorable President Mrs. Bidhya Devi Bhandari inaugurated the official program of launching Digital Signature.
Electronic Transaction...
Nepal DDOS Attack Trends & How You Should Respond
5th May 2021, Kathmandu
Digital Network Solutions is all set to organize DDOS Attack trends in Nepal and How we should respond to the webinar on 12th May 2021 from 11 a.m.
The...
Importance Of Web Application Firewall
The firewall which controls input, output or access to, from or by an application or services is known as an application firewall. The application firewall is generally created for the control...
Reports Suggest 1 in 5 Risky Links Contain Malware
3rd July 2020, Kathmandu
Malware is pretty much everywhere these days. It’s in mobile applications, websites, or our emails. In fact, threat actors are targeting remote workers across the globe by redirecting...
Please Report any Threats in the name of the Cyber Bureau: Nepal Police
11th May 2020, Kathmandu
The Cyber Bureau of Nepal Police has published a statement on social media urging everyone to remain vigilant. The statement also addresses the recent character assassination activities that...
How to Update Web Browsers for Secure Browsing
10th May 2021, Kathmandu
The World Wide Web accessing software application also known as web browsers or simply “browser” is used to access and view websites through internet. Some of well-known browsers...
Google patches Chrome zero-day, eighth one in 2021
19th July 2021, Kathmandu
Eight security vulnerabilities, including a high severity zero-day flaw exploited in the wild, are inscribed by Google Chrome.
Chrome’s new version (91.0.4472.164) has been released for Windows, Mac, and...
Patches for iOS Security Wi-Fi Vulnerability Recently Announced
27th July 2021, Kathmandu
A seemingly harmless WiFi hack was recently warned to iPhone owners all around the world that it was not only potentially harmful but also a real menace. That...
NIBL Says It Never Asks Its Customer To Share Any Credentials
April 09, 2020, Kathmandu, Nepal
Nepal Investment Bank Limited (NIBL) requests its users not to provide banking passwords and any sort of data to anyone. NIBL has urged no one to provide any...
2018 Checkpoint Threat Report, The Future of Cyber Security
Check Point Infinity architecture delivers consolidated Gen V cybersecurity across networks, cloud, and mobile environments.
Download 2018 Security Threat Report - CHECKPOINT
Nepal Rastra Bank Direct Banks To Do “Information Security Audit”
Friday, September 13, 2019, Kathmandu
Nepal Rastra Bank has been alerted after the Chinese nationals hacked the Nepali bank’s system on September 1st. This is the serious issues that should be addressed, the...