Cyber Security Awareness Is About Both Knowing And Doing
August 8, 2016 - 23rd cybersecurity awareness program at Davi Higher Secondary School, Birtamode Jhapa which is one of the prominent management school and college or great college In Jhapa district.
The...
How The Cell Phones Of Spring Breakers Who Flouted Coronavirus Warnings Were Tracked
April 06, 2020, Kathmandu
The Trump administration has focused on tracking the spread of coronavirus since its global outbreak. For this purpose, it wants to use America’s smartphone location data in order...
Apple Air Tag Tracker Hacked and Reprogrammed by a Security Researcher
17th May 2021, Kathmandu
Apple Air Tag may have some security matters that could be exploited by hackers to modify the firmware of the device. Apple had released the Air Tag last...
7 Tips for Implementing a Personnel Security Program
17th October 2021, Kathmandu
For what reason does it appear to be that probably the main things in life are regularly those that are the most ignored? For instance, a Personnel Security...
Finance Minister Said: NRB To Alert Regarding Cybersecurity Issues
Thursday, September 6, 2019, Kathmandu
After six days since the Chinese hackers looted crores of rupees from various banks by designing fake visa cards, Finance Minister Dr. Yuvraj Khatiwada has talked about...
Cobalt Application Security Platform, Pentest as a Service
16th April 2021, Kathmandu
Cobalt, a Pentest as a Service (PtaaS) platform that simplifies the security and compliance needs of DevOps-driven teams with workflow integrations and high-quality talent on-demand. Cobalt offers a...
Everything You Need to Know About the Malvertising Mayhem
Everything You Need to Know About the Malvertising Mayhem
What is Malvertising?
Malvertising is a pet name for malware that’s delivered through online advertising techniques. The ads look authentic. Often, legitimate third-party marketing companies distribute...
NRB’s Cyber Resilience Guidelines: Safeguarding the Payment Sector in Nepal
1st September 2023, Kathmandu
Rastra Bank's Payment Systems Department has taken a proactive step by introducing a comprehensive set of guidelines called the "NRB's Cyber Resilience Guidelines."
These guidelines are tailored to authorized...
Android 5.0 Lollipop Is Set To Roll Out To The Sony Xperia Z3
Sony announced a brand new Xperia Z3 smartphone on September 2014 which was released the same month that comes up with an Android OS v4.4.4 (KitKat) up-gradable up to v5.0.2 (Lollipop)...
Specialize In Information Security And Ethical Hacking Courses
Information is an important means for the growth and success of every organization. Keeping the information and vital data secure is the main duty of every employee in the company in...
Guar Of National Breach Highlights The Risk Of Accidental Data
As the use of an employee-owned device is increased in the enterprise, the risk of accidental data disclosure through apps and services that are outside the control of that enterprise such as emails, social...
Researchers Discover a Serious Security Flaw in 5G Network
4th July 2019 Kathmandu
Many places in Nepal still don’t have proper access to the fourth generation of networks (4G). However, this doesn’t stop the world-renowned communication companies to develop, test and...
Microsoft Warned about an Alert Over Sneaky Phishing Attack
3rd August 2021, Kathmandu
Microsoft has issued an alert about a crafty phishing attack.
Microsoft's Security Intelligence team has issued an alert to Office 365 users and administrators to watch out for a...
What Exactly Is Security Information Management (SIM) ?
Security information management(SIM) is an industry terminology that is related to information security relating to the gathering of data mainly log files into a central memory for trend analysis.
Generally, SIM products...
Google To Release Your location Data To Help Fight Coronavirus Pandemic
April 06, 2020, Kathmandu
What exactly is Google capable of? What better time than a global pandemic - to really give the world a clear glimpse of Google's capability. Google is publicly...
Online Payment System Targeted By Cyber Criminals
April 10, 2020, Kathmandu, Nepal
Doing everything online might be the easiest and efficient way of life, but it surely is not the safest. With the increasing number of cybercrimes, there are...
Instagram Has a New Plan to Strengthen its Anti-bullying Feature
8th April 2021, Kathmandu
Instagram – a social media platform that is preparing to launch a new feature that will strengthen its anti-bullying feature.
These new features may be an AI device. This...
Tesla Employee Turns Down $1 Million, Avoids a Cyberattack Bump
29th August 2020, Kathmandu
Earnest employee saves the day and prevents a major cyber attack at Tesla.
A Tesla employee turned down an offer worth $1 Million and helped the FBI arrest a...
OpenSea NFT Marketplace Bug Allows Hackers to Steal Crypto Wallets
16th October 2021, Kathmandu
In the course of recent weeks, a few instances of lost crypto wallets have been accounted for and tweeted via online media stages. Clients have been grumbling around...
Apple iPhone 11 Series Ships With A Security Flaw: Here Are The Details
22 September, Kathmandu
Only a few days have passed since brand-new iPhone 11, iPhone 11 Pro and iPhone Pro Max have been released, and security researchers have already detected some flaws in the...
Which Security Control Is The Hacker Affecting ?
A security contravention is an event that leads to unauthorized access of data, files, services, or the device itself. The nature of the incident or the level of the breach can...
How to Snoop With Kali Linux on Bluetooth Contrivances
10th October 2021, Kathmandu
Bluetooth has become a major component of our lives. Bluetooth contrivances are utilized every day by many individuals around the globe. Most of them, though, have no conception...
Researchers Detail Modus Operandi of Shiny Hunters Cyber Crime Group
25th August 2021, Kathmandu
ShinyHunters, a notorious cybercriminal underground group that's been on a knowledge breach spree since last year, has been optically canvassed probing companies' GitHub repository ASCII text file for susceptibilities which will be abused to...
Explore The Ultimate Journey in Cybersecurity and Digital Forensics
27th August 2022, Kathmandu
People who work with digital forensics in information security are on the front lines of the fight against cybercrime.
People who collect, process, preserve, and analyze computer-related evidence. They...
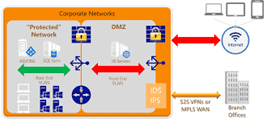
Building Secure Data Access,Threats And Countermeasures
The network security contains the policies taken to monitor and prevent misuse, access, modification or denial of a network accessible resources and computer network. Network security includes the authorization of access...
CyberSecurity Awareness For Gauradaha Jhapa Students
61st Cyber Security Awareness Program for School Chaun High School Gauradaha Jhapa, Nepal sponsored by Nurse Manju Sangraula, Virginia USA. Bishnu Priya Rijal (DCnepal.com) Chitwan, Nepal, January 28, 2017 - Cyber...
Companies Can Find the “X” Factor For Cybersecurity Compliance
11th April 2021, Kathmandu
Cybersecurity threat, a malicious act that seeks to damage data, steal data, or disrupt digital life in general. Cyber threats include computer viruses, data breaches, Denial of Service...
Best Ways To Secure Your Stored Data
The data-eccentric security is a method of protection that gives high preference to the safety of data and information instead of the security of servers, networks or applications. The data-eccentric security...
5 Safety Tips While Using Social Media That Saves You More
The 21st century has been tech savvy. Digitization all over the world has made human to move into different mediums like social media, websites, and email to share the information. Moving...
Russia’s Critical Sectors Under APT Group ChamelGang’s Radar
10th October 2021, Kathmandu
The assault vector of Russian state-supported progressed diligent danger (APT) assailants is stretched out across different nations. Various cybercriminal bunches from Russia have designated a few worldwide basic...