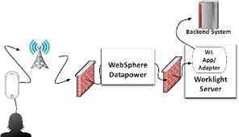
Governments Hold Lots Of Personally Identifiable And Commercially Sensitive
Data masking also known as the data obfuscation is the act of hiding the original data with random data or characters. The prime reason for implementing masking to a data sector...
Promoting A Physical Security Mental Model For Personal Firewall
A personal firewall is an application that controls network traffic from and to a computer, allowing and denying communications based on a security policy. Generally, it works as an application layer...
Get To Know Junos OS Flow Based Stateful Firewall
In computing, a firewall is a network security system that controls and monitors the incoming as well as outgoing network traffic as according to security rules that are already determined. Generally,...
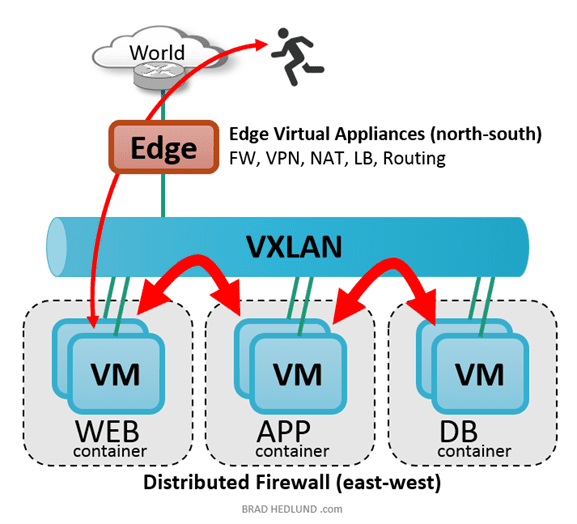
Building Secure Data Access,Threats And Countermeasures
The network security contains the policies taken to monitor and prevent misuse, access, modification or denial of a network accessible resources and computer network. Network security includes the authorization of access...
Sensor Access Technology Nepal: Access Control Systems
The various control is the selective restriction of access to a resource or other place in the sector of information security and physical security. Login credentials and Locks are the two similar mechanisms of...
Security Issues For Service Providers, Emerging wiFi Hacking Problems
Interaction Program “Securities Issues in ISP in Nepal”
With lots of excitement and enthusiasm, many specialized people along with VIP members participated in a program to give their valuable speech on “Securities...
Interactions On ISP Securities And Issues In Nepal, ITSERT-NP
Nepalese ISP's actions to protect their network may already be an important factor in cyber security. To minimize the Cyber threat in ISP, The ITSERT Nepal is going to be organized the...
FAQs: Guidelines For Usage Of Digital Signature In Nepal
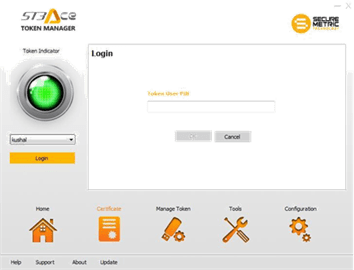
Steps for Using Tokens from Nepal Certifying Company (NCC)
Insert the Nepal Certifying Company Pvt. Ltd. provided token, Wait for the dialogue box to appear.
Click on the Open folders to view files,...
Mobile Security Gateway Secures The Delivery Of Voice And Data
The Mobile Secure Gateway (MSG) is a term that is used for software or hardware appliance that gives secure communication between a mobile application and the respective back end source generally...
How To Increase App Security Through Mobile Phone Authentication ?
Mobile security also known as mobile phone security has become an essential factor day by day in mobile computing. Nowadays some personal and business information is stored on smartphones. Many business...
Cryptography For Network And Information Security
14th August 2019, Kathmandu
Cryptography is used by the information security to change the readable information into a secured form which ensures that it can only be accessed by the authorized user...
Defense In Depth A Simplistic Model
Defense in Depth: The information must be protected throughout its life span from the initial development of the data to the destruction of that information. No matter what whether at rest...
Why And How The CISO Job Description Is Changing ?
Chief Information Security Officer, The senior executive officer, is regarded as a Chief Information Security Officer (CISO) who is responsible for establishing and maintaining the enterprise strategy, vision, and program to make...
What Exactly Is Security Information Management (SIM) ?
Security information management(SIM) is an industry terminology that is related to information security relating to the gathering of data mainly log files into a central memory for trend analysis.
Generally, SIM products...
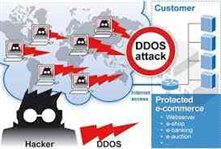
DDoS Attack Protection And Mitigation Service Employs
Intrusion Prevention System (IPS). The Intrusion Prevention Systems (IPS) are the network security appliances that maintains the systems and networks activities for malicious acts. It is also called as Intrusion Detection and...
Best Ways To Secure Your Stored Data
The data-eccentric security is a method of protection that gives high preference to the safety of data and information instead of the security of servers, networks or applications. The data-eccentric security...
A Brief History Of Internet Security, Technology Hit The Market
History of information security. From the ancient day's communication, military captains and diplomats knew the essence to have specific methods to protect the confidentiality of correspondence and have some mechanism to detects...
Can Computer Security Deliver Business Value?
Information Technology security sometimes called as computer security is the information security that is applied to technology which most often relates to the same form of computer system, but it is necessary to know...
Demand For IT Security Experts Outstrips Supply
Information security is the way of protecting information from unauthorized use, access, inspection, disclosure, modification, disruption, recording, perusal or destruction. It is also referred to as InfoSec in short form. It is used as...
Why Information Security Advisory Board (ISAB) ?
The secretary of the Information Security Advisory Board (ISAB) gives the department an independent idea and suggestions on all the factors of information security standards, requirements, guidelines, and practices.
The Information Security...
Why Your Organization Need A Customer Identity Management ?
The Identity Access Management(IAM) System is a framework for business procedures that maintain the management of electronic information identities. This framework contains the technologies that are needed to support identity management.
The...
IT Risk Management Audit And Assurance Application
IT risk management is the application of the risk management methodology of information technology so that the IT risks could be managed. It can be taken as a component of greater...
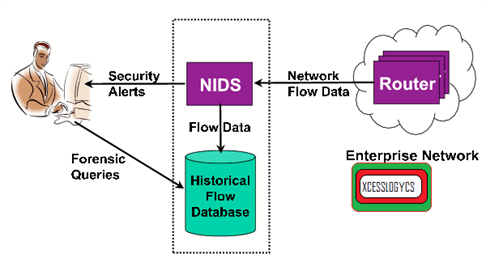
Conduct Forensic Analysis Of Suspicious Activity In A Network
The Intrusion Detection System (IDS) is a software application or a device that monitors system or network activities for policy violation or malicious activities and gives electronic reports to the management...
Importance Of Web Application Firewall
The firewall which controls input, output or access to, from or by an application or services is known as an application firewall. The application firewall is generally created for the control...
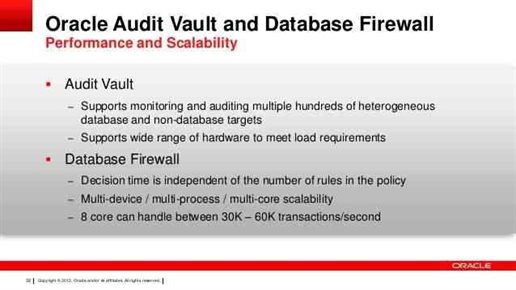
Protect Database From Security Threats, Secure IT
The database security deals with the use of wide ranges of information security prevention to secure databases that generally include the data, the database systems, database applications or stored functions, the...
The Importance Of Data Protection, Shree Khanal
Mr. Shree Khanal, the founding chair from SQL Pass Nepal has given his speech on “The Importance of Data Protection: a Real- World Example.”
He primarily focused his speech on data security,...
Security And Privacy Issues In E-Government, Pavan Duggal
Mr. Pavan Duggal is the President from India has been working on Cyberlaw Asia.Net on Security Issues of E-Government Applications. He is the pioneering of Cyberlaw and the Director of the...
Best Practices For Enterprise Security
Enterprise Network Security relates to the real-time defense and preventive measures implemented by an enterprise to protect the business network and threats that may breach or paralyze the network system. This...
Guar Of National Breach Highlights The Risk Of Accidental Data
As the use of an employee-owned device is increased in the enterprise, the risk of accidental data disclosure through apps and services that are outside the control of that enterprise such as emails, social...
Start A Security Company ? Dr. RamHari Subedi
Dr. Ramhari Subedi and his team recently formed a company called Cyber Security Institute International based in Washington D.C. Our company goal is to provide Cyber Security Awareness campaign, and other...