Specialize In Information Security And Ethical Hacking Courses
Information is an important means for the growth and success of every organization. Keeping the information and vital data secure is the main duty of every employee in the company in...
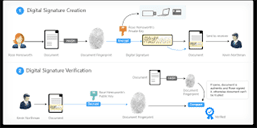
What exactly is a digital signature?
Just as a handwritten signature is affixed to a printed letter for verification that the letter originated from its purported sender, digital signature performs the same task for an electronic message.
A...
Security Analyst, Cyber Security Degrees
The main job of an information security analyst is to plan and implement security procedures to ensure the computer networks and systems of an organization is protected. As the number of...
What Is Information Security Policy ? Cyber Security Law And Policy
Information Security Policy is a collection of policies implemented by an organization to make sure that all the information technology users within the grasp of the organization or its branches stay...
Why Digital Signature? What Is Digital Signature ?
Radiant InfoTech Nepal is a Certifying Authority licensed by Controller of Certifying Authorities, under Government of Nepal. Radiant operates under the guidelines set by Information Technology Act. Radiant is the first...
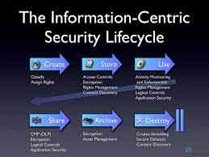
Data Security Is A Risk Management Problem
The significant database vulnerabilities that are present today for more than a decade ago are buffer overflows and SQL injection. These vulnerabilities provide access for the attackers who may compromise the...
5 IT Security Skills Certifications on the Rise
As it comes to regarding information security, people only read the headlines to see that those with harmful intent find new and effective ways regularly to access and misuse the protected...
Policies to Mitigate Cyber Risk, Learn Information Security Cyber Law
Information Technology Security Alerts in Nepal. Majority of Nepalese people use the electronic devices to acquire information, and a similar number of people use electronic devices to make transactions of that...
The Importance Of A Security Culture Across The Institution
A significant impact is made by the employee's behavior to information security in organizations. The culture concept can help different parts of the organization that concerns about information security within the...
The Top 10 Highest Paying Jobs In Information Security Domain
The organizations are doubling their demands for talented and qualified security professional since the concerns about hacking, data security, and privacy; identity thefts are increasing these days with many high-profile data breaches...
Cyber Security Must Be Strengthened In Nepal
The first meeting of the Cybercrime Division Nepal Expert Group brought together cyber experts from around Nepal to review current cybersecurity programs and provide advice for future activities. The cyber threat...
Digital Crime And Fraud Investigation By Pyramid
Pyramid Cyber Security & Forensic (P) Limited is an ISO 9001-2008 and ISO 27001-2005 certified boutique Digital Forensic and specialized Information Security Solutions & Services Company.
Digital Crime and Fraud Investigation
Digital Forensic...
Which Physical Security Measure Is In Place ?
You are testing physical security measures as part of a pen test team. Upon entering the lobby of the building, you see the entrance has a guard posted at the lone...
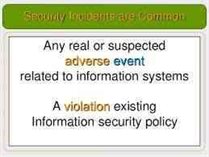
Which Security Control Is The Hacker Affecting ?
A security contravention is an event that leads to unauthorized access of data, files, services, or the device itself. The nature of the incident or the level of the breach can...
Russian Hackers Have Created A USB Stick
Russian Hacker made a killer pen drive, which changes TV and Computer into ashes.
Its name only is kept as gadget killer. Because this surely can change all your computer and TV...
What Is Computer Forensics ?
Computer Forensics refers to information collected from and about computer systems that are admissible in a court of law. Because computer data is intangible, can be easily modified and is a...
87% Of Android Phones Are Vulnerable To Hackers
Smartphone, an ancient but good friend, is the thing that we always keep on carrying. Wherever we go, with whomever we go in any new or old destination we always bring...
How To Design A Useful Incident Response Policy ?
Organizations should be prepared to detect and respond to incidents before they occur. This plan should be embodied in an accident response policy. For example, The Carnegie Mellon University CERT Coordination...
Internet Communication Security Counter measurers
A wide variety of countermeasures are needed to protect an organization from the assortment of threats. The counter measure's used to defend Internet-based threats are not much different from those protecting...
What To Do After You’ve Been Hacked
10 Steps to Defeat Hacking Attacks (And What to Do after You’ve Been Hacked)
Through this article, I’m going to tell you the first steps that you need to take to defeat...
Cyber Security is the Protection of Internet Connected Systems
According to the cybersecurity records 2014 back and half of 2015 was projecting 2019 for the forthcoming years. The job about cyber security which is, so top and the responsibility for...
Social Engineering psychological manipulation of its Types
Social engineering is a non-technical method of intrusion hackers which relies heavily on human interaction and often involves tracing people and breaking standard security procedure. It is one of the significant...
Hacker Threatens S. Korean Nuclear Power Plants If Ransom Not Paid
6th March 2015, Kathmandu
A hacker that claims to have compromised sensitive data belonging to South Korea’s power plants has threatened to share the information with other countries if a ransom is...