BlackMatter Group Demands $5.9 Mn Ransom After Attacking NEW Cooperative
28th September 2021, Kathmandu
The Biden administration is trying to investigate ransomware attacks, attackers are targeting the critical infrastructures in the country. The farm services provider is the latest victim of ransomware...
144496 Cyber Attacks in India in the Last Three Years
28th September 2021, Kathmandu
According to the Indian Parliament, over a million cyber attacks were reported in the last three years. The data, which was collected by the CERT division of India,...
Conti Ransomware Attacks on Rising – CISA, FBI, NSA Issue Joint Alert
27th September 2021, Kathmandu
According to the Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI), the Conti ransomware attacks have increased in the U.S and international organizations.
With...
New Cyber Campaign “Armor Piercer” Targets Indian Government Officials
27th September 2021, Kathmandu
Cyberattacks and malicious campaigns are increasing in a rapid way. According to research from Cisco Talos shows a cyber-campaign, tracked as Armor Piercer, targeting the government and defense...
Singapore Businesses Struggling to Cope with Network and Ransomware Attacks
24th September 2021, Kathmandu
Cybersecurity standards remain a serious concern for organizations as Singapore is expanding its digital transformation capabilities. According to Barracuda Networks, network and ransomware attacks have become a hurdle...
Ongoing Credential Harvesting Campaign Targets Government Agencies in APAC
24th September 2021, Kathmandu
Ongoing Credential Harvesting Campaign Targets Government Agencies in APAC, EMEA
Security researchers found an issue of credential harvesting campaigns targeting government agencies across seven countries in the Asia-Pacific (APAC),...
6 Fundamental Skills Required Pursuing a Career in Digital Forensics
22nd September 2021, Kathmandu
Digital forensics is a better career path to grow in 2021 and beyond. The cybercriminal's malicious activities are giving trouble to the digital forensics specialists. Attackers these days...
How to Keep Your Crypto Wallet Safe? Cryptocurrency is illegal in Nepal
14th September 2021, Kathmandu
Are you trying to keep your Crypto wallet safe? Also, do you know Cryptocurrency is illegal in Nepal? Let’s find out the detail in this article below.
Cryptocurrency is...
What are Network Protocols and How Are They Used?
13th September 2021, Kathmandu
Network Protocols are the set of rules for formatting and processing data. Network Protocols are used for communication between different devices. These rules explain how data and information...
CISSP Certification Training in Kathmandu Nepal
11th September 2021, Kathmandu
CISSP (Certified Information Systems Security Professional) Certification Training in Kathmandu Nepal
Are you looking to take training for CISSP certification in Kathmandu Nepal? If yes, you have landed on...
8 Internet Safety Tips for Kids on How to Safe Online
9th September 2021, Kathmandu
What is online safety?
Simply, online safety is the act of staying safe online. Which is commonly referred to as internet safety, e-safety, and cyber safety.
Online safety is about...
Ransomware Recovery Solutions in Nepal
8th September 2021, Kathmandu
OneCover Private Limited is now providing ransomware solutions in Nepal.
OneCover with its fellow company, Scrutiny Ransomware Solution is now all set to provide ransomware solutions to all the...
Most Common Types of Network Security Attacks Explained
6th September 2021, Kathmandu
The peril of network security attacks is mounting as businesses transition to a remote work environment and embrace sophisticated technology.
The IT (Information Technology) and security professionals’ roles are...
Ransomware Vulnerabilities That Could Bring Down Your Organization
6th September 2021, Kathmandu
Today, 266 susceptibilities are associated with ransomware, and assailers are increasingly exploiting these impuissances to launch devastating ransomware attacks. Ergo, identifying and remediating these susceptibilities needs to be...
U.S. Cyber Command Warns of Ongoing Attacks Exploiting Atlassian Confluence Flaw
5th September 2021, Kathmandu
The U.S. Cyber Command on Friday admonished of perpetual mass exploitation endeavors within the wild targeting a now-patched critical security susceptibility affecting Atlassian Confluence deployments that would be abused by unauthenticated assailants to...
This New Malware Family Using CLFS Log Files to Avoid Detection
5th September 2021, Kathmandu
Cybersecurity researchers have disclosed details about an incipient malware family that relies on the Mundane Log File System (CLFS) to obnubilate a second-stage payload in registry transaction files...
WhatsApp Photo Filter Bug Could Have Exposed Your Data to Remote Attackers
4th September 2021, Kathmandu
A now-patched high-astringency security susceptibility in WhatApp's image filter feature could have been abused to send a malignant image over the messaging app to read sensitive information from...
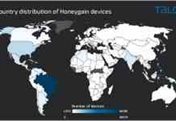
Cybercriminals Abusing Internet-Sharing Services to Monetize Malware Campaigns
3rd September 2021, Kathmandu
Threat actors are capitalizing on the growing popularity of proxy war platforms like Honeygain and Nanowire to monetize their own malware campaigns, once again illustrating how assailants are...
Attackers Can Remotely Disable Fortress Wi-Fi Home Security Systems
3rd September 2021, Kathmandu
Incipient susceptibilities have been discovered in Fortress S03 Wi-Fi Home Security System that could be potentially abused by a malevolent party to gain unauthorized access with an aim...
Delhi High Court to Hear Appears to Facebook and WhatsApp in October in Privacy...
1st September 2021, Kathmandu
Delhi high court to hear appears to Facebook and WhatsApp in October in privacy policy matters.
The Delhi supreme court verbalized it'll auricularly discern in October the appeals of...
LockFile Ransomware Bypasses Protection Using Intermittent File Encryption
29th August 2021, Kathmandu
An incipient ransomware family that emerged last month comes with its own bag of artifices to bypass ransomware aegis by leveraging a novel technique called "intermittent encryption."
Called LockFile,...
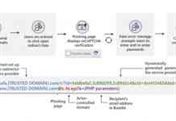
Microsoft Warns of Widespread Phishing Attacks Using Open Redirects
29th August 2021, Kathmandu
Microsoft is an admonishment of a widespread credential phishing campaign that leverages open redirector links in email communications as a vector to illude users into visiting malevolent websites...
What are Supply Chain Attacks by cybersecurity?
28th August 2021, Kathmandu
Today, a growing number of hackers are adopting sophisticated implements and techniques to assail a company’s Supply Chain Management and wreak havoc in business operations.
In today’s evolving digital...
Biden Administration and Tech Giants Come Together to Raise Bar on Cybersecurity
28th August 2021, Kathmandu
To address the ascending cyber threat landscape in the U.S., Biden Administration and tech giants such as Google, Microsoft, Apple, and IBM, have converged to ameliorate the security...
Cisco Issues Critical Fixes for High-End Nexus Gear
28th August 2021, Kathmandu
Networking giant issues two critical patches and six high-rigor patches.
Cisco Systems relinquished six security patches tied to its high-end 9000 series networking gear ranging in paramountcy from critical,...
Win10 Admin Rights Tossed Off by yet another Plug-In
28th August 2021, Kathmandu
Then again, you don’t even require the authentic contrivance, in this case, a SteelSeries peripheral since emulation works just fine to launch with full SYSTEM rights.
It’s not just...
Researchers Detail Modus Operandi of Shiny Hunters Cyber Crime Group
25th August 2021, Kathmandu
ShinyHunters, a notorious cybercriminal underground group that's been on a knowledge breach spree since last year, has been optically canvassed probing companies' GitHub repository ASCII text file for susceptibilities which will be abused to...
38 Million Records Exposed from Microsoft Power Apps of Dozens of Organizations
25th August 2021, Kathmandu
More than 38 million records from 47 different entities that believe Microsoft's Potency Apps portals platform were inadvertently left exposed online, bringing into sharp focus an "incipient vector...
Users Can Be Just As Dangerous As Hackers
12th August 2021, Kathmandu
Among the quandaries stemming from our systemic failure with cybersecurity, which ranges from decenniums-old software-development practices to Chinese and Russian cyber-attacks, one quandary gets far less attention than...
Bugs in Managed DNS Services Cloud Let Attackers Spy on DNS Traffic
12th August 2021, Kathmandu
Cybersecurity researchers have disclosed an incipient class of susceptibilities impacting major DNS-as-a-Accommodation (DNSaaS) providers that could sanction assailers to exfiltrate sensitive information from corporate networks.
"We found a simple...